Risk Assessment
A-to-Zerto Glossary of Terms
Overview
Risk assessment is an essential part of business continuity planning, along with business impact analysis (BIA). It helps organizations understand the threats they face and the resulting risks those threats pose to their business. The results of a risk assessment inform risk prioritization and risk mitigation investments.
Related Topics
What Is Risk Assessment ?
In general, and as part of the risk management process, risk assessment identifies and evaluates all potential risks faced by an organization. These include risks to strategy (competition, innovation, geo-politics, economics, and social environment), finances (access to capital, taxes, reporting), compliance and governance (regulatory, ethics, trade, etc.), and operations (business disruptions, fraud, employment practices, etc.).
Within the context of business continuity , risk assessment mainly covers operational risks that would result in a business disruption, preventing the organization from delivering its products and/or services to customers. Natural disasters, system failures (power grid blackout, hardware failure, etc.), or bad actors (cyber/ransomware attack, terrorism) are common causes of disruption.
Risk assessment identifies all the threats and vulnerabilities that comprise risk. It is primarily concerned with detecting the sources of disruption, possible areas of impact, and the likelihood that a potentially disruptive event will occur. It also documents existing strategies and measures already in place to mitigate the impact of said risks.
How Is Risk Assessment Related to Risk Management ?
Risk assessment is a key element of business continuity planning and risk management overall.
In business continuity, it informs the business continuity plan which is part of operational risk management. Operational risks concern failed processes or events that cause disruption to business operations.
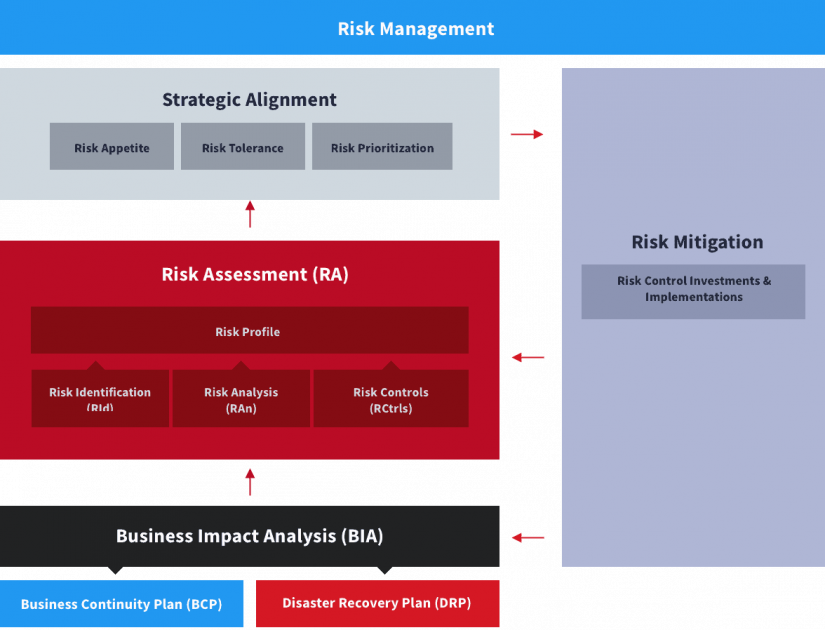
Figure 1: Risk management process for operational risks
One of its key outputs is a risk map that represents the risk profile of the organization, and that will enable the business to assess its risk profile against its overall risk appetite and tolerance. It will ultimately inform decisions about what investments are needed to mitigate or eliminate risks outside of the organization’s risk tolerance.
Since risk management also covers strategy, finances, and compliance and governance risks —which are all mainly managed through business or corporate strategy— risk assessments are also done for those other areas.
Risk Management Definition
Risk Management Process for Operational Risks - Overview
What Is Included in Risk Assessment?
Risk assessment involves several steps:.
- Risk identification: Inventory of the threats, vulnerabilities, and resulting risks an organization faces to its infrastructure, resources, and processes.
- Risk analysis. Determine who and what would be affected, and what the impact would be. This would heavily leverage the results of a BIA. At this stage, risks are qualitatively scored for likelihood and impact.
- Risk Controls. Identify and propose actions that can mitigate, or even eliminate, the identified risks. This stage documents any resulting update to a risk’s score.
Risk Map: an Organization's Risk Profile
A successful risk assessment produces a risk profile that assigns a quantitative value to the identified risks based on their likelihood and level of impact (impact vs. likelihood). The risk profile is usually represented as a two-dimensional matrix, or risk map, as shown in figure 2.
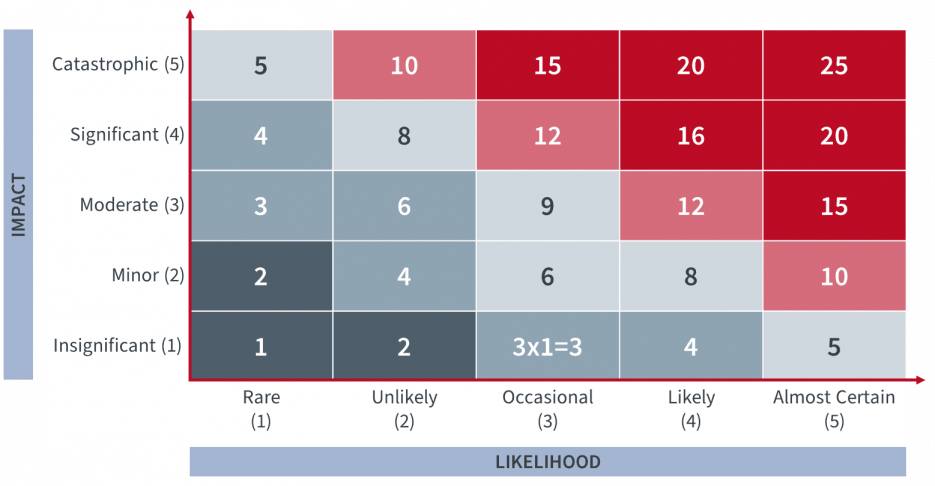
Figure 2: Risk map as a 2x2 matrix
Once identified and analyzed risks are set on the map, it can be used to align the risk profile with the organization’s risk appetite and tolerance.
What's the Difference Between Risk Assessment and Business Impact Analysis (BIA)?
A BIA explains the effects and severity of losing key business functions and/or processes, disregarding what is responsible for that loss. Rather than pinpointing the cause, a BIA focuses on understanding the impact of the loss to determine the recovery plan and timeframes to resume operations. A BIA can be undertaken without a risk assessment.
As already mentioned, a risk assessment analyze potential threats and vulnerabilities that make up a risk, then assesses the likelihood of that risk happening. It also describes how the business would be affected, that is, what resources and functions would be impacted. This leads to the prioritization—i.e., tiering—of these risks.
Essentially, risk assessment identifies potential risks, assesses their severity, and determines the best course of action to mitigate or eliminate them. A BIA is typically leveraged or executed when assessing the severity — or impact— of each identified risk.
When combined, the BIA and risk assessment enable a business to prioritize critical risks or threats based on their likelihood and impact.
Risk Assessment: 3 Key Starting Points for Effective Business Impact Analysis
Risk Assessment, BIA, SLA, RTO and RPO: What’s the Link? MTD and MTDL
Risk, Threat, Vulnerability, and Mitigation: What is the Relationship?
Although the various concepts involved in risk assessment define different things, they are often used interchangeably. It’s important to understand the distinction between them:
- Threat. This is a person/actor or event that can potentially have a negative impact on a valuable or critical business resource or asset. Threats can be intentional (ransomware attack), unintentional (human error), and natural (floods, hurricanes, etc.). “Risk” is often used to mean “threat.”
- Vulnerability. This is a weakness of a critical business resource or asset, as a result of the quality of that resource and/or its environment. A threat will exploit one or more vulnerabilities associated with a resource or asset.
- Risk. This is the result of a vulnerability being exploited by a threat. There is a probability a risk will occur (likelihood), and it poses a negative impact or loss of value. This is represented on a risk map.
- Mitigation or Risk Control. This action reduces or eliminates the negative impact of a threat. This can be done by eliminating the threat, reducing vulnerabilities, limiting damage where the impact cannot be eliminated, and increasing the speed and effectiveness of recovery until the threat becomes uneventful. Mitigation can be a combination of all the above.
Evolution of a Risk Through the Risk Management Process
Let's Illustrate how the assessment of risk can evolve when going through the risk management process.
For example, a hurricane is a threat to a company’s datacenter located in an increasingly frequent path for hurricanes. The building hosting the datacenter is vulnerable to high-speed winds and flooding. The risk is a full shutdown of the datacenter. This would cripple business functions relying on the IT systems and applications run in the datacenter. This risk, set as a tier-1 risk, is noted “A” on the map shown in figure 3. Due to its high priority, this risk is evaluated for potential mitigation actions.
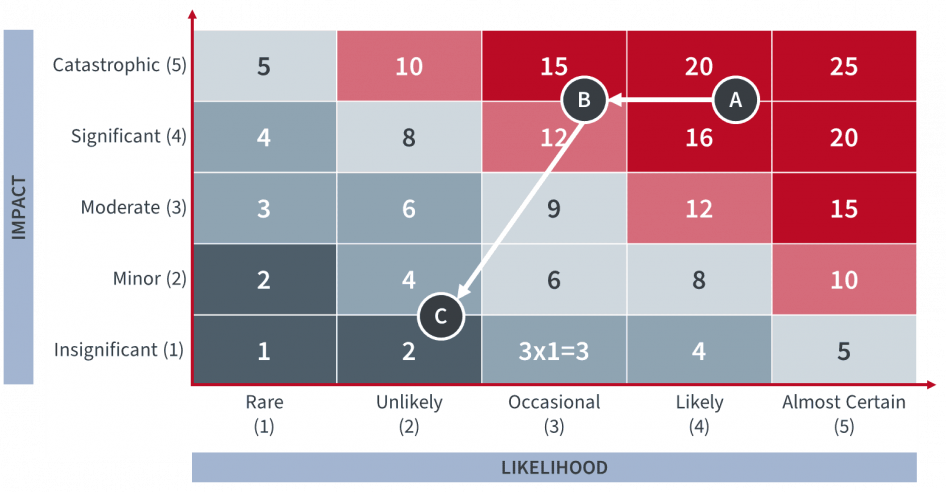
Figure 3: Evolution of the assessment of a risk on a risk map
As a mitigation strategy, two levels of risk control are being identified and implemented.
First, the building is to be hardened to sustain very high winds and to undergo additional construction to make it more flood-resistant (retaining walls, pumps with auxiliary generators). These actions will reduce the vulnerability of the datacenter, which in turn will lower the risk posed by a hurricane. The risk moves to “B” on the map.
Second, a secondary site is to be set in the cloud with a solution that enables fast failover and recovery. This will lower even further the risk posed by a hurricane, even though the threat would remain present, by significantly reducing its impact on the business. The risk now moves to “C” on the map.
In this example —focused on IT infrastructure— while overall the threat of a hurricane still has a high likelihood, from a business standpoint, the risk posed by it has been greatly reduced through its mitigation strategy. Therefore the likelihood of the risk posed by a hurricane is now way lower, while its potential impact on the IT system and applications should be very limited.
Other Consideration: Risk Velocity
Risk velocity is a concept recently added to some risk analyses. Risk velocity represents the time until impact, or the time frame within which a risk may occur. It differentiates between risks that have some level of predictability and those that have none.
A blizzard or a hurricane, for example, is usually forecasted a few days in advance. A labor strike can be foreseen by weeks or months and therefore has a low to very low velocity. However, a grid blackout or cyberattack does not provide any warning and happens instantly: these types of risks are considered high velocity.
Risk velocity can be included in risk score calculation to help with risk prioritization. It can also be added to a risk map—as shown in figure 4 using coloring—and filtered for each risk velocity level (if shown on a dashboard).
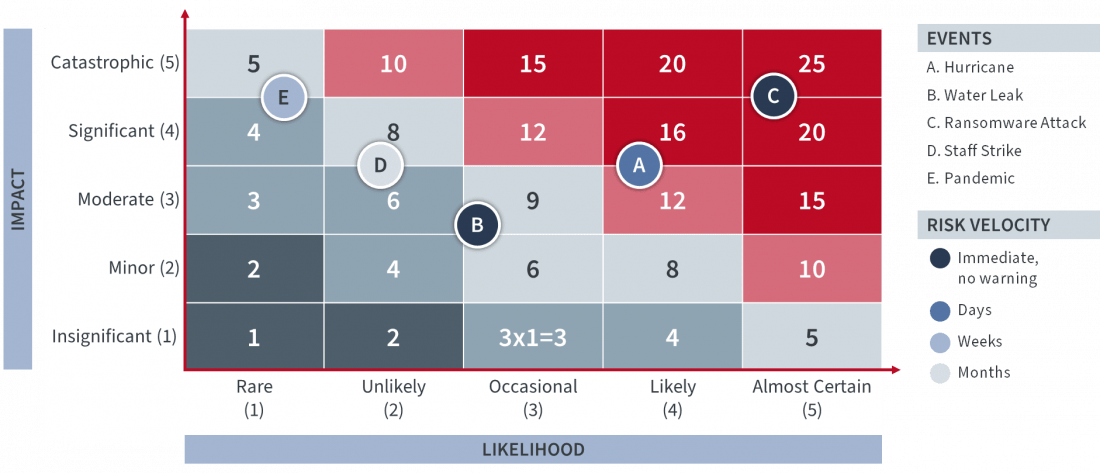
Figure 4: Example of risk velocity representation on a risk map
However, velocity shouldn’t overshadow risk assessment. For example, complying with an upcoming trade regulation that prevents shipping to certain regions may be rated as low velocity at the time of assessment because it is to be enforced in three years. However, three years of preparation might be required to fully mitigate the risk posed by the regulation. From a business continuity standpoint, this risk would gain priority to avoid future business disruption.
Zerto as a Risk Control Tool
One way to mitigate the risk of a significant disruption is to deliver speed and effectiveness over the recovery phase.
Zerto, a Hewlett Packard Enterprise company, does just that. It ensures that IT systems remain resilient through the identified potential disruptions and can deliver the RPOs and RTOs that meet the most stringent SLAs against maximum tolerable time or data loss metric (MTD and MTDL).
By providing the best RPO and RTO at scale in the market, Zerto supports true business continuity.
Zerto Solution Overview
Zerto for Disaster Recovery
Other Resources
LATEST FROM ZERTO SEE ALL
Resource Center
Discover and access content from Zerto and 3rd parties (IDC, Gartner, ESG, etc.) related to business continuity.
Essential Guide: Business Continuity
Get everything you need to know about business continuity in one guide.
Business Resilience Blog Series
Learn more about business resilience and how organizations can achieved it.
What is Zerto?
Learn about Zerto and how it can help you solve your disaster recovery challenges.