RSA 2020: Zerto Challenges the Cybersecurity Industry to Rethink Data Protection and Recovery
As the IT Resilience Platform has evolved, so has its use cases. Zerto has seen every recovery scenario possible through its customers. One of the fastest growing recovery scenarios for Zerto users is ransomware.
Our customers organically began using our replication-based solution to solve for cyber attacks and ransomware that traditionally fall under backup use cases. As we dove deeper into the world of ransomware, we realized why our customers are using us instead of backup tape and disk to recover from ransomware.
Traditional backup and recovery solutions are outdated, and users aren’t confident in their ability to recover from backup tape and disk.
So this year, Zerto decided to attend the RSA Conference in San Francisco. RSA has been a flagship conference in cybersecurity for decades and remains at the forefront of innovations within the space.
We didn’t attend RSA as a cybersecurity vendor, we attended as a company challenging both cybersecurity and IT professionals to rethink their approach to recovery and risk mitigation.
The Zerto Booth
Our Zerto team was excited and well equipped for this conference. From Monday to Thursday each of us had insightful conversations with CISOs, security analysts, IT professionals and many more unique roles within the space.
After multiple demos and in-depth conversations, it was clear that our message was resonating.
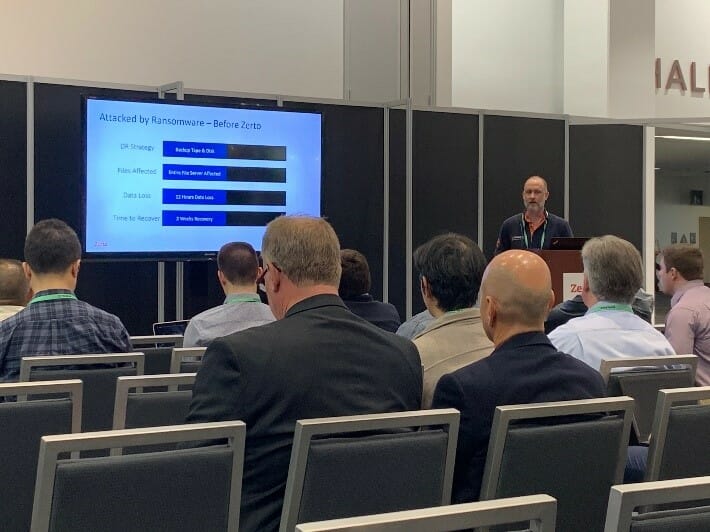
Tencate, a Zerto Customer, presents at RSA
Jayme Williams, Systems Engineer at Tencate Fabrics, presented his Zerto success story to all sorts of attendees.
He explained how his organization was attacked by ransomware before and after and discussed the start differences between using backup tape and disk vs. Zerto’s Continuous Data Protection to recover from ransomware.
Throughout the week we had excellent conversations and gained many insights. I’d like to share some with you:
- Post-attack recovery has become a critical component of a cybersecurity framework.
- CIOs and IT leaders are understanding that traditional recovery isn’t working in today’s world
- Cyber-attacks, specifically ransomware, is becoming much more sophisticated and damaging for both individual users and large organizations
We truly enjoyed our experience at RSA and can’t wait for next year. In the meantime, I urge you to download Zerto’s Cyber Attack Survival Kit to learn more about how Tencate survived a ransomware attack with Zerto and how Zerto can help you mitigate the risk of downtime and data loss due to ransomware.