
Hypervisor-Based Replication vs. Storage Replication
There are many types of replication solutions for data protection, but today I want to focus on two of the most common types: hypervisor-based and storage. Both replication types can come in the form of snapshot replication or real-time replication with variations between asynchronous, synchronous, and near-synchronous. They both may also be included as features of hypervisors and storage arrays, or as third-party solutions with additional features and benefits. Let’s delve into the pros and cons of these replication technologies in more detail.
Pros and Cons of Hypervisor-Based Replication
Hypervisor-based replication integrates with, or is directly embedded in, a hypervisor and is designed to replicate virtual machines and virtual storage objects residing within the hypervisor ecosystem. This may include virtual disks (VMs) or raw device mapping (RDM).
Pros of Hypervisor-Based Replication
- Granularity—Hypervisor-based replication can replicate individual VMs or even individual virtual disks and these can be recovered individually as needed.
- Hardware-Agnostic—Operating within the virtualized environment of the hypervisor allows hypervisor-based replication to be agnostic from the underlying physical hardware and storage so the environment can be nearly any vendor or hardware model.
- Software-Only—Most hypervisor replication solutions are software-only consisting of virtualized components. There is no need of hardware components. The exception to this could be in some backup solutions that use proprietary physical backup appliances.
Cons of Hypervisor-Based Replication
- Virtual-Only—Hypervisor-based replication can only replicate VMs and disks within the hypervisor. It cannot protect any data or machines outside of the hypervisor.
- Hypervisor-Specific—Hypervisor-based replication is tied to specific hypervisor vendors and would likely support only one or maybe a small number of available hypervisor vendors.
Pros and Cons of Storage Replication
Pros of Storage Replication
- No Additional Cost—Storage replication is often built into storage arrays or as a feature of virtualized storage solutions at no additional cost. The replication features vary by vendor.
- Any Stored Data——Any data stored on the array, or within the storage area of the solution, may be replicated by that storage solution. This could be storage used by a hypervisor or other storage volumes used by physical servers, container solutions, or other types of applications.
Cons of Storage Replication
- Lack of Granularity—Storage replication can typically only replicate at the volume-level (one volume or more) meaning everything – no matter how large the volume size — will be replicated a single logical unit. Recovery is therefore of the entire volume as well. This does not easily allow for failover or recovery at a granular level.
- Hardware-Specific—Storage replication is often specific, not just to a vendor but to a specific model of hardware, meaning you must have the same or similar hardware at the replication target. This limits the flexibility of using storage from multiple vendors across locations.
Combining Storage and Hypervisor-Based Replication
Both forms of replication have their pros and cons, but they do not have to be mutually exclusive. In this age of information, as data is rapidly growing and digital transformation is everywhere, the need for disaster recovery is higher than ever. Taking a multi-pronged approach can make a disaster recovery solution even more powerful and less vulnerable to one of the biggest threats today: cyberattacks.
Cyberattacks like ransomware often target data protection solutions to try to disable the ability of an organization to recover. Having more than one data protection solution in place can add another layer of protection by having one more system or set of credentials for attackers to compromise.
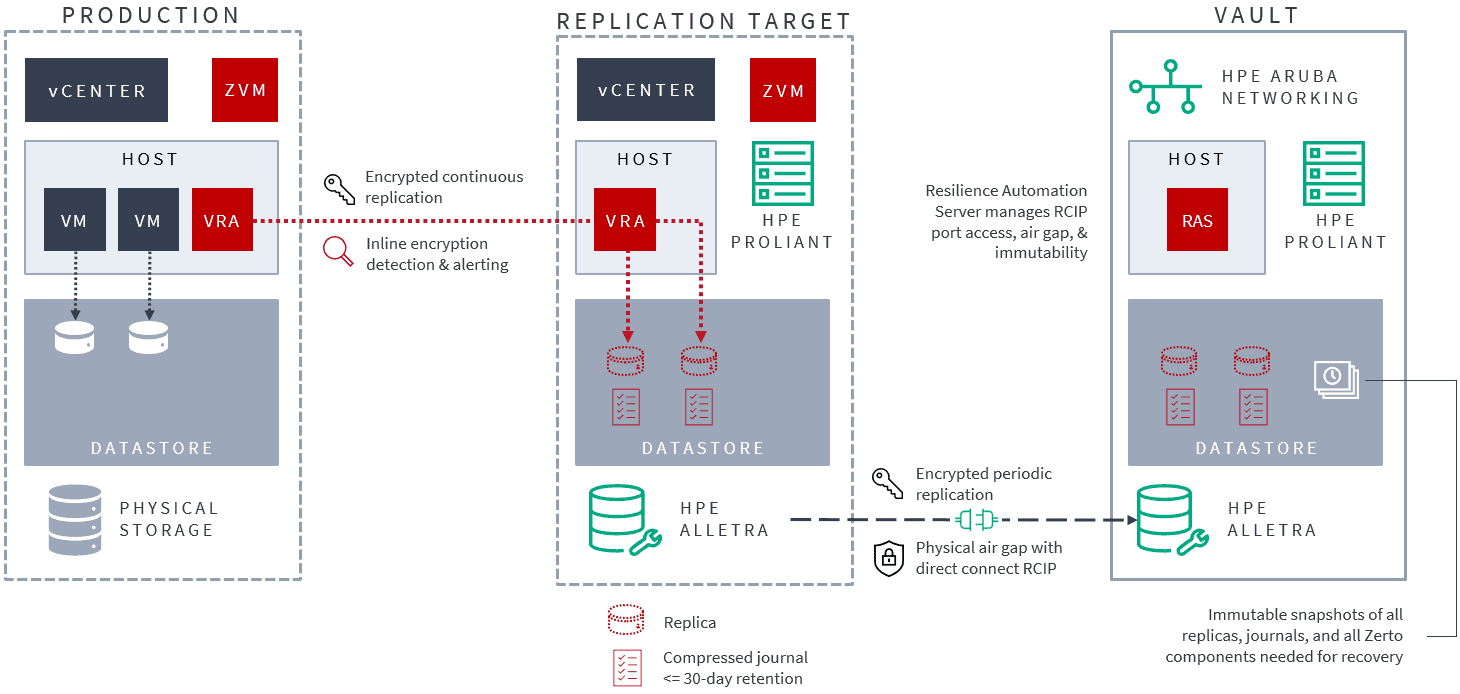
Take the example of the Zerto Cyber Resilience Vault, as shown below. It combines both Zerto hypervisor-based near-synchronous replication with storage-based snapshot replication to provide the ultimate protection of an isolated, air-gapped vault.
Zerto Cyber Resilience Vault Architecture diagram
Using both Zerto replication from the primary site to the replication target and then storage replication between the HPE Alletra arrays from the replication target to the vault allows the secondary replication network connection to be isolated over a dedicated Fibre Channel (FC) network. The storage replication is managed from the isolated vault, and the only way to access the data stored in the vault is by physically managing it onsite.
This is a great use case where two replication technologies, used together, are far more powerful than one alone. Combining both the granular and real-time replication of Zerto with the volume-based and snapshot-based replication of the HPE Alletra creates a vault architecture with the recovery options needed to fully recover from a ransomware attack, even if it compromises the primary DR site.
Conclusion
Not all replication technologies are created equal, nor should they be. Choose the technology, or technologies, that best meet your organization’s need and look for ways to combine them for maximum benefit.
Learn more about hypervisor-based replication and about the Zerto Cyber Resilience Vault.
 David Paquette
David Paquette 