Achieving Data Immutability with Zerto
In today’s digital landscape, data is one of the most valuable assets for any organization. Ensuring its security is paramount, especially in the face of increasing cyber threats and stringent regulatory requirements. Implementing technologies such as data immutability can help address those needs.
Why is Data Immutability Important?
Data immutability is a critical component for organizations to store data in a way that it cannot be altered or deleted once written. This capability is crucial for several reasons:
- Cyber resilience: With the rise of ransomware attacks and other cyberattacks, having immutable data ensures that your critical information remains untouched and recoverable. Even if attackers gain access to your systems, they cannot modify or delete immutable data, providing a reliable recovery point.
- Regulatory compliance: Many industries are subject to strict regulations that mandate the protection and retention of data. Immutability helps organizations comply with these regulations by ensuring that data cannot be tampered with, thus maintaining its integrity and authenticity.
- Validated data integrity: Immutable data guarantees that the information remains in its original state, which is essential for maintaining trust in the data. This is particularly important for financial records, legal documents, and other sensitive information where accuracy is critical.
Approaches to Achieve Data Immutability with Zerto
When it comes to achieving immutability with Zerto, there are several effective methods. One such approach is through the Zerto Cyber Resilience Vault. This product combines two major cyber resilience components: an immutable data vault and an isolated recovery environment known as a clean room.
Another approach is utilizing Zerto’s Extended Journal Copy (EJC) capability. This feature works in conjunction with object storage protocols, leveraging the underlying object lock capabilities.
Achieving Data Immutability with the Zerto Cyber Resilience Vault
What is the Zerto Cyber Resilience Vault?
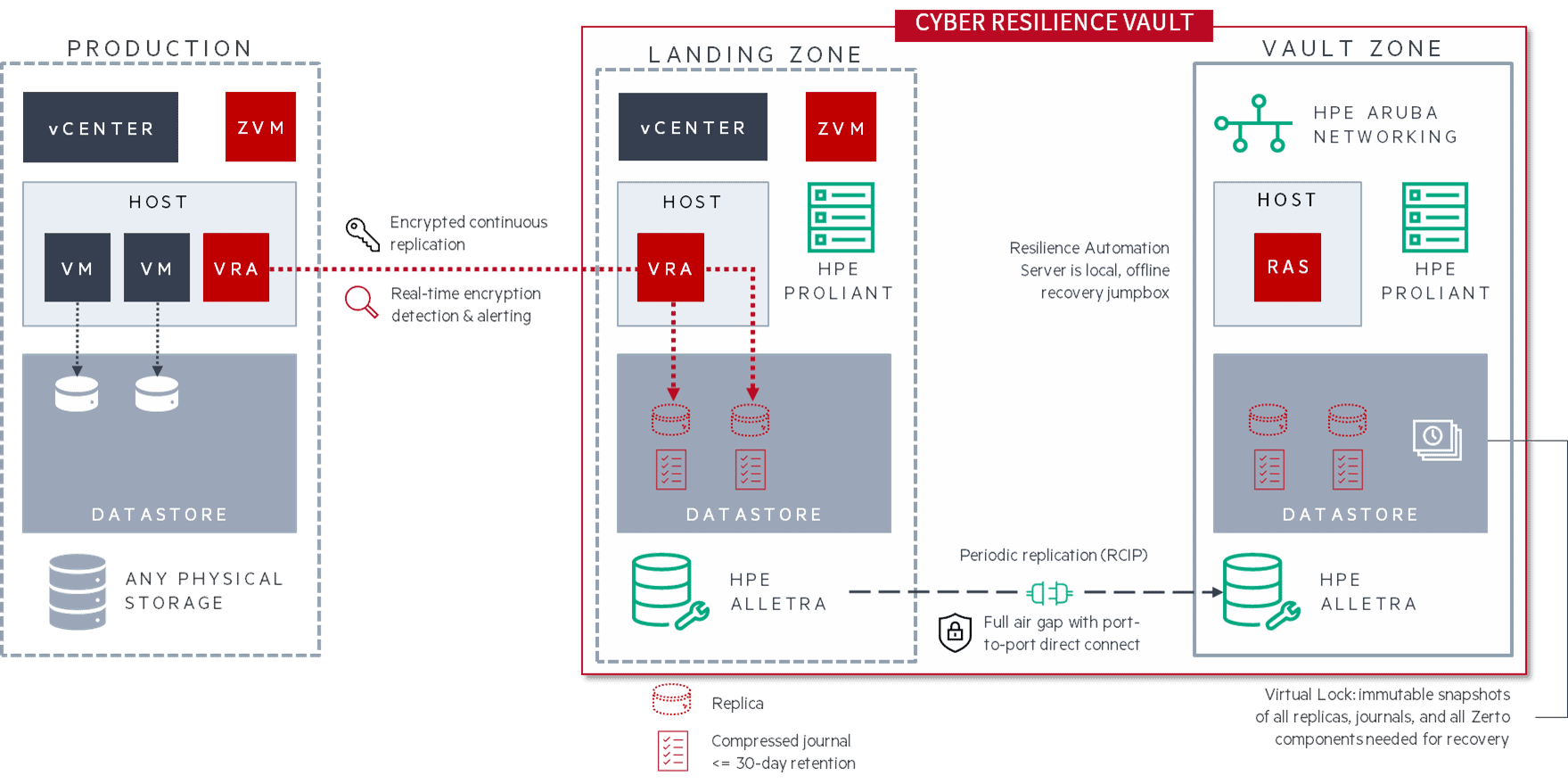
The Zerto Cyber Resilience Vault is an offline, locked-down vault that combines Zerto’s recovery software with the power of HPE Alletra Storage MP, HPE ProLiant servers, and HPE Aruba Networking. The Zerto Cyber Resilience Vault offers rapid air-gapped recovery with an immutable data vault and built-in clean room on high-performance infrastructure.
How Does Zerto Cyber Resilience Vault Work?
There are three main components that make up the Zerto Cyber Resilience Vault:
Landing zone—Securely paired with the production site, the vSphere-based landing zone can be local or remote and can also serve as a traditional DR target if located offsite. The zone serves as a replication target for continuous data protection (CDP) with Zerto. The Zerto journals and all associated replicas are attached to virtual appliances running on HPE ProLiant, with their datastores on HPE Alletra vLUNs. As writes are mirrored for the journal, they are also inspected using real-time encryption detection from Zerto for the earliest warning of possible infections.
Cyber Resilience Vault—The vault itself, co-located with the landing zone, also includes HPE ProLiant and HPE Alletra. The isolated vault, or clean room, is fully air gapped and has no access to the internet or production network. Since there is no centralized control plane, the vault does not have an exposed management port and does not have any single point of compromise. The HPE Alletra on the recovery site and the HPE Alletra inside the vault use a proprietary protocol for point-to-point replication of all data from the recovery site, including the Zerto journals and replicas. This approach combines the best of synchronous replication (e.g., hyper-low RPOs and high performance) and traditional asynchronous approaches (e.g., higher latency tolerances and reduced storage consumption).
Vault automation—The Resilience Automation Server (RAS) inside the vault is a lightweight virtual machine (VM) that works with native services in HPE Aruba and HPE Alletra to control key cyber resilience measures. These measures include:
-
- Enabling and disabling replication ports on the HPE Alletra to maintain a truly isolated vault bubble
- Creating snapshots and making them immutable with HPE Alletra’s locking technology
- Recovering the Zerto Virtual Manager, journals, and replicas to rebuild a clean Zerto deployment inside the vault should everything else outside it be compromised
- Logging all activity inside the vault to keep an audit record
Zerto Cyber Resilience Vault Architecture
Achieving Data Immutability with Zerto Extended Journal Copy
What is Zerto Extended Journal Copy?
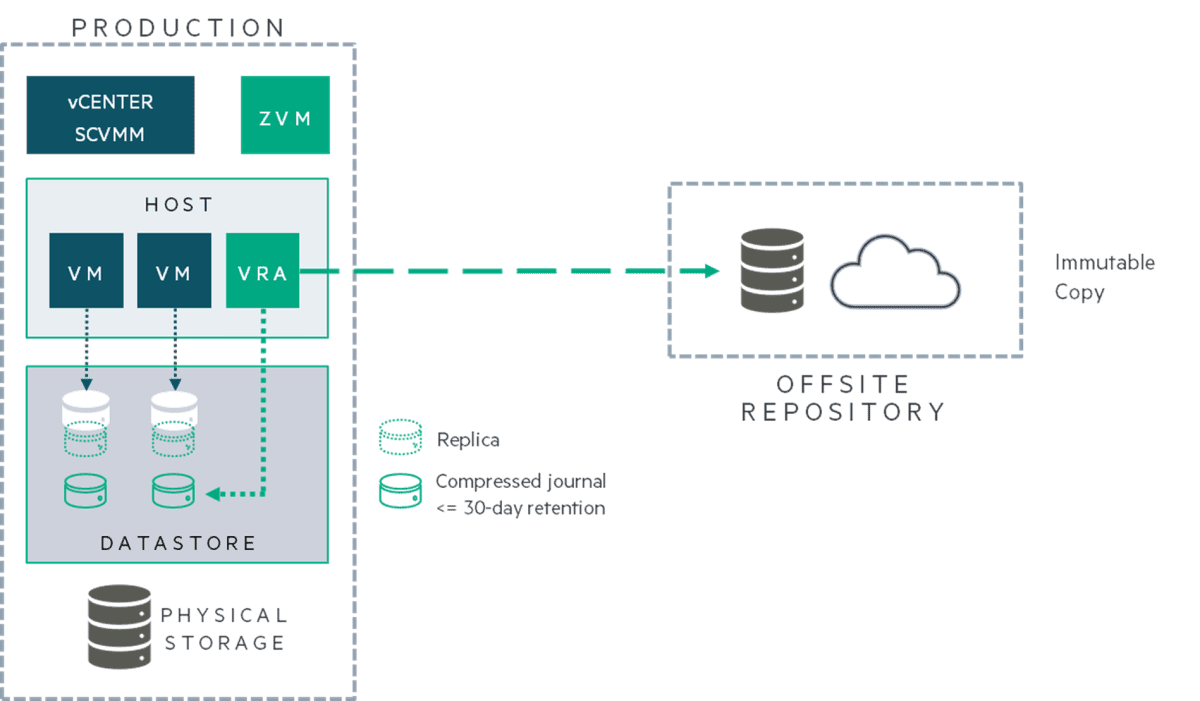
The Zerto Extended Journal Copy enables storing data for extended periods, defining retention policies, and restoring the data with granularity down to the VM level. You can define the target on which to keep the data, and for how long to retain the data, in accordance with your organization’s needs and regulations.
How Does Zerto Extended Journal Copy Work?
Copy process—The first time Extended Journal Copy runs, it reads and writes all data to the data repository (full Retention set). Each following run only adds changes since the last run, using the existing full set.
Repository and Retention—Zerto makes Retention sets immutable to protect against ransomware and malicious changes. Once enabled, these sets can’t be deleted or modified until their expiry date, leveraging an Object Lock API. This feature works with Amazon S3, Azure Blob, or S3-compatible storage.
Zerto Architecture with Offsite Immutable Copy (Extended Journal Copy)
Combining data immutability with Zerto’s continuous data protection, or benefiting from data immutability built into the Zerto Cyber Resilience Vault, you have two very robust options to strengthen your cyber resilience and be prepared to face future ransomware attacks.
For more information on either option, get in touch with us.
 Andrew Silva
Andrew Silva