Managing Cyberthreats to Combat Ransomware Part 3: Cybersecurity Frameworks
As we continue with our third and final blog in this series on managing cyberthreats, we’ll explore frameworks from the National Institute of Standards & Technology and Center for Internet Security, which together provide time-tested knowledge and best practices used to combat ransomware.
National Institute of Standards & Technology
National Institute of Standards & Technology (NIST) develops cybersecurity standards, guidelines, best practices, and other resources to meet the needs of US industries, federal agencies, and the broader public. NIST produces everything from specific, immediately actionable information to long-term research that anticipates both technology advances and future challenges, such as advanced cyberthreats.
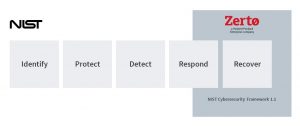
The NIST Cybersecurity Framework 1.1 has five core categories that provide robust cybersecurity and dramatically reduce the risk of a cyberattack:
- Identify—Forms the foundation of the framework. These controls develop an organizational understanding for effective management of cybersecurity risk to systems, people, assets, data, and capabilities. When an organization understands the business context, resources that support critical functions, and related cybersecurity risks, it can focus and prioritize its risk management strategy and business needs. These activities include asset management, business environment, governance, risk assessment, and risk management strategy.
- Protect—Safeguards delivery of critical services, limiting or containing the impact of a potential cybersecurity event. This covers identity management and access control, awareness and training, data security, information protection processes and procedures, maintenance, and protective technology.
- Detect—Identifies cybersecurity events quickly. Detection comprises anomalies and events, security continuous monitoring, and detection processes.
- Respond—Takes action after a cybersecurity incident is detected, containing the impact of the incident. Response activities include planning, communications, analysis, mitigation, and improvements.
- Recover—Maintains plans for resilience and restores any capabilities or services that were impaired by a cybersecurity incident. The Recover function recovers quickly to normal operations to reduce the impact of a cybersecurity incident. This includes recovery planning, improvements, and communications.
By following each step of the NIST Cybersecurity Framework, you can put your organization in a position to not only respond effectively to cyberthreats, but also proactively mitigate future risk.
The Center for Internet Security’s Critical Security Controls
The Center for Internet Security (CIS) Critical Security Controls is an international volunteer community of individuals and institutions. Their goal is to identify the important real-world cyberattacks that affect enterprises daily, translate that knowledge and experience into positive and constructive action for defenders, and share that information with a wider audience.
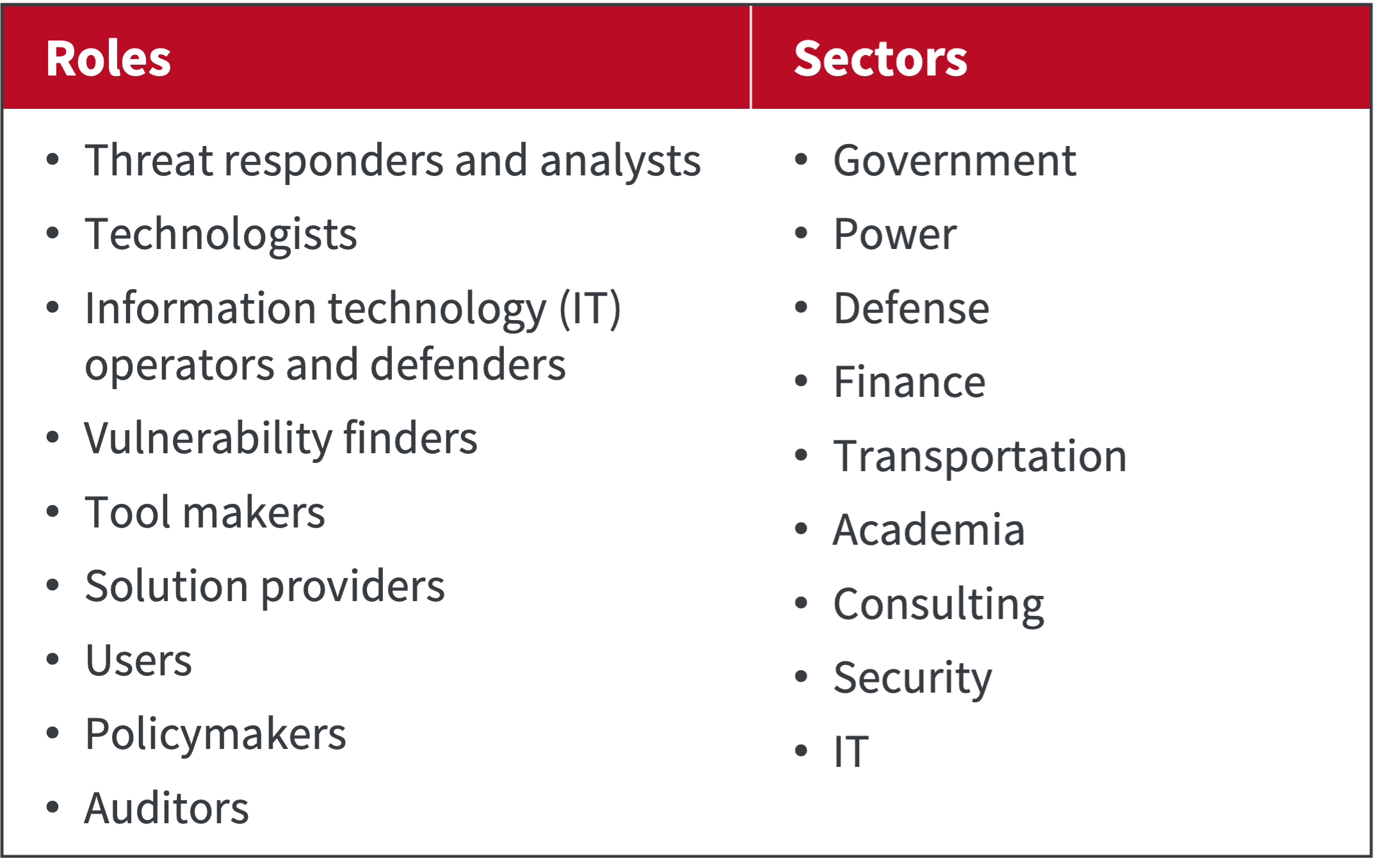
The CIS Controls reflect the combined knowledge of experts, companies, and governments representing every part of the ecosystem:
These experts have banded together to create, adopt, and support the CIS Controls. The current version of controls (v8) includes:
- Inventory and control of enterprise assets
- Inventory and control of software assets
- Data protection
- Secure configuration of enterprise assets and software
- Account management
- Access control management
- Continuous vulnerability management
- Audit log management
- Email and Web browser protection
- Malware defenses
- Data recovery
- Network infrastructure management
- Network monitoring and defense
- Security awareness and skills training
- Service provider management
- Applications software security
- Incident response management
- Penetration testing
As a comprehensive pool of volunteer knowledge spanning nearly every realm of business, the CIS Controls provides practical, applicable advice you can use to address everyday cybersecurity concerns.
With the NIST and CIS, we’ve only touched the surface of framework resources available. But both entities provide solid cybersecurity frameworks that organizations can follow for best practices and ever-changing cybersecurity needs.
Zerto: Protect Your Data, and Be Stress-Free about Cyberattacks
To learn more about managing cyberthreats to combat ransomware check out part 1 and part 2 of this blog series and feel free to contact us!
 Andrew Silva
Andrew Silva