Air Gap in Data Protection
A-to-Zerto Glossary of Terms
What Is an Air Gap in Data Protection?
Air gapping is security by isolation. An air gap is a security measure that physically and/or logically isolates a system from unsecured networks. The primary purpose is to create a barrier that prevents unauthorized access to sensitive data.
Air-gapped systems are commonly utilized in environments where data security is of utmost importance such as, government agencies, military, and critical infrastructure sectors.
Types of Air Gaps
Physical Air Gap
A physical air gap refers to the complete physical isolation of a computer or network from other networks, including the internet. This means there is no physical connection (such as Ethernet cables, fiber optics, or wireless connections) that links the air-gapped system or network to any external devices or networks.
The only way to transfer data in and out of a physically air-gapped system is through manual methods, such as carrying data on a USB flash drive or other removable media. This method is considered highly secure because it significantly reduces the attack surface for cyber threats.
Logical Air Gap
A logical air gap, on the other hand, refers to the use of software and configuration strategies to create a separation or isolation between systems or networks. This does not remove the physical connectivity but uses technologies like firewalls, virtual LANs (VLANs), and other network segmentation techniques to control and limit access between isolated systems and the wider network or internet.
Logical air gaps are designed to reduce the risk of unauthorized access or data leakage between the segregated parts of the network, but since the systems remain physically connected, the security is not as robust as a physical air gap.
The convenience of a logical air gap comes at the cost of increased vulnerability to sophisticated cyber-attacks that can potentially bypass logical controls.
Can Cloud Be Used as an Air Gap?
Cloud can be used to implement air-gapping. It falls under the logical air-gap type, as previously defined.
Cloud air gap leverages the cloud as infrastructure as a service (IaaS) and uses digital technologies and advanced technics for access control as a way to implement the air gap between your environment and the cloud where your data might be stored.
Air Gap and the 3-2-1 Rule
The 3-2-1 rule can be broken down into three simple parts:
- Keep 3 copies of data, including all production data and two backup copies.
- Store backup copies on 2 different types of storage, including any combination of on-premises, cloud, or offline options.
- Ensure 1 backup copy is stored at an off-site location, such as a public cloud server.
While still a foundational rule for an effective backup strategy, the 3-2-1 rule has evolved to adapt to new threats such as cyberattacks—among them, ransomware attacks. In this scenario, a bad actor may gain access to the whole network, and therefore all the copies of the data, including potentially copies stored in the cloud, if not managed and secured in a different fashion.
Air gapping is one way to strengthen the 3-2-1 rule, along with immutable backups. This adds the requirement to have one copy of the data offline, or air-gapped, and forms the 3-2-1-1 rule. For a logical air gap, that means enhanced security (hardware, access management with additional credentials) and maybe using different accounts in the case of cloud air gap.
The 3-2-1 Backup Rule
What’s the difference: Immutability vs Isolated Environment vs Air-Gapping?
Immutability
Immutable data is data that is in an unalterable state. Data is said to be in WORM format (write once, read many).
However, backup immutability is about securely storing data that cannot be modified or deleted for a set period. Once past that retention period, the backup can be replaced.
This characteristic provides the ability to manage the backup infrastructure, in terms of storage volume and cost, while ensuring the integrity of the data, making it an effective defense against ransomware and malicious tampering, as attackers can't alter the backups to compromise data recovery processes.
For instance, an immutable data vault is designed to store immutable backups of your data for a set period.
Isolated Recovery Environment
An isolated recovery environment, is a secure, controlled space that's segregated from the main network. It's used for safely analyzing and recovering from cyberattacks without risking further contamination of the network or compromising the recovery process.
Air-Gapping
As already mentioned, air-gapping is the mechanism used to create the actual isolation, or segregation between environments—production vs recovery. And the air gap can be physical or logical.
Immutable Backup
Types of Immutable Data Vaults
Combining Immutability, Isolated Environment, and Air-Gapping
When used together over an air-gapped network, an immutable data vault and an isolated recovery environment offer a powerful combination for cyber resilience.
- The air gap provides physical isolation, significantly reducing the risk of remote cyberattacks reaching the backup or recovery environments.
- Meanwhile the immutable data vault ensures that, even in the event of a network compromise, a clean, unaltered copy of critical data is available for recovery.
- The isolated recovery environment offers a safe space to restore data and systems without exposing them to ongoing threats.
This synergy enhances an organization's ability to recover from cyber incidents swiftly and securely, leveraging the strengths of both approaches to provide a robust defense against a wide range of cyber threats.
The Importance of Isolated Recovery Environments and Immutable Cyber Data Vaults
Rapid Air-Gapped Recovery with Zerto Cyber Resilience Vault
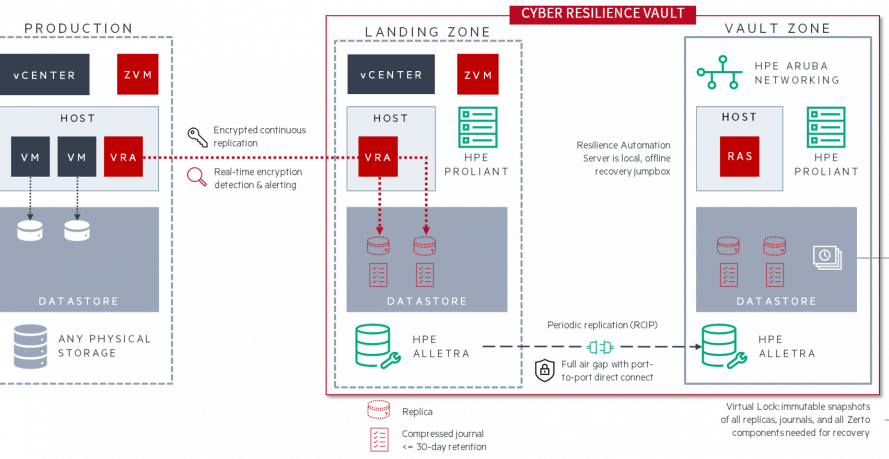
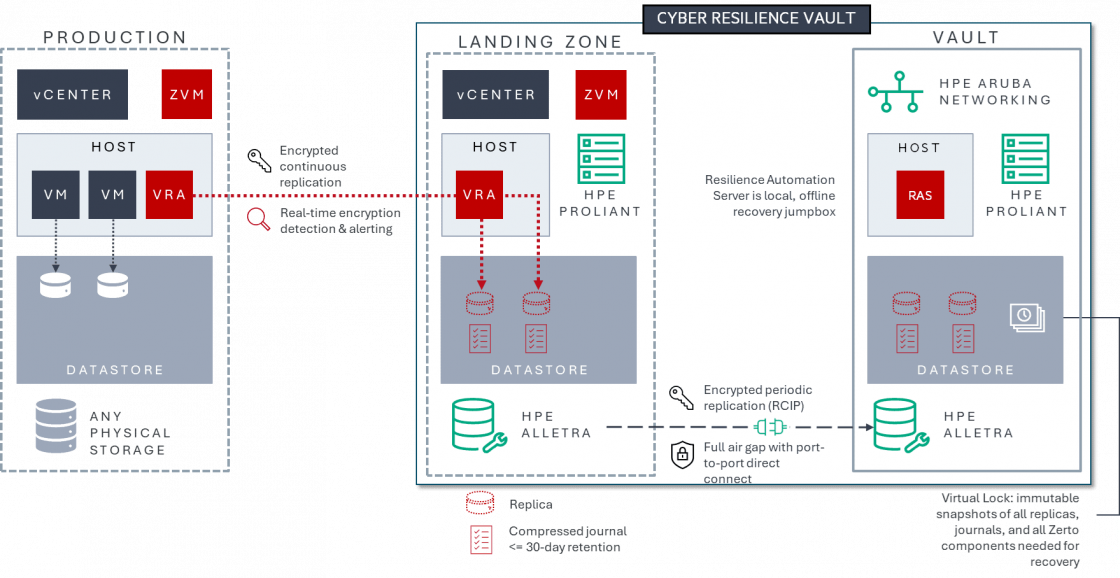
Many vault solutions claim complete isolation or air-gapped systems. However, most vaults have numerous connections to outside networks for management, providing only partial network isolation.
The Zerto Cyber Resilience Vault is a truly isolated, offline environment that uses physical and logical air gaps to guarantee true isolation.
Zerto Cyber Resilience Vault architecture diagram - Click to zoom in
Leveraging zero-trust principles, the Zerto Cyber Resilience Vault enables rapid air-gapped recovery in the event of a serious cyberattack. If all else fails, Zerto's disconnected clean room, combined with a secure immutable data vault, allows organizations to get back up and running within a matter of hours.
Zerto Cyber Resilience Vault
Understand the Zerto Cyber Resilience Vault
Understand the Zerto Cyber Resilience Vault
To exit, click outside the video
Other Resources
LATEST FROM ZERTO SEE ALL
More on Cyber Data Vaults
Discover and access content related to cyber vaults in Zerto's resource center.
Modern Data Protection: What Is It and Why Should You Care?
Learn about data protection principles and technologies, and understand why it is important to prevent data loss and mitigate downtime .
Ransomware Is a Growing Cyber Threat: Are You Ready for It?
From the definition of ransomware, description of how a ransomware attack unfolds, right down to cyber resilience and ransomware recovery, we cover everything in this ultimate Ransomware Recovery guide.
What is Zerto?
Learn about Zerto and how it can help you solve your data protection and recovery challenges.