Cyber Resilience
A-to-Zerto Glossary of Terms
Overview
Cyber resilience refers to the ability of businesses to mitigate the risk of damage to their data and operations and to bounce back unscathed once attacked. Instead of relying on a traditional disaster recovery plan, modern businesses need to transition to a cyber-resilient approach to ensure always-on service.
Related Topics
What Is Cyber Resilience ?
Today’s organizations know it is a matter of when, not if, they will experience a cyberattack. Cyber resilience is the ability to prepare for, respond to, and recover from a cyber-attack once it occurs.
Cyber resilience addresses this issue by looking past prevention to consistently ensure the integrity of your critical data to mitigate risk. This type of resiliency requires a recovery solution that guarantees access to all your data, without gaps or data loss, in the event of an attack so your operation can get back up and running without delays.
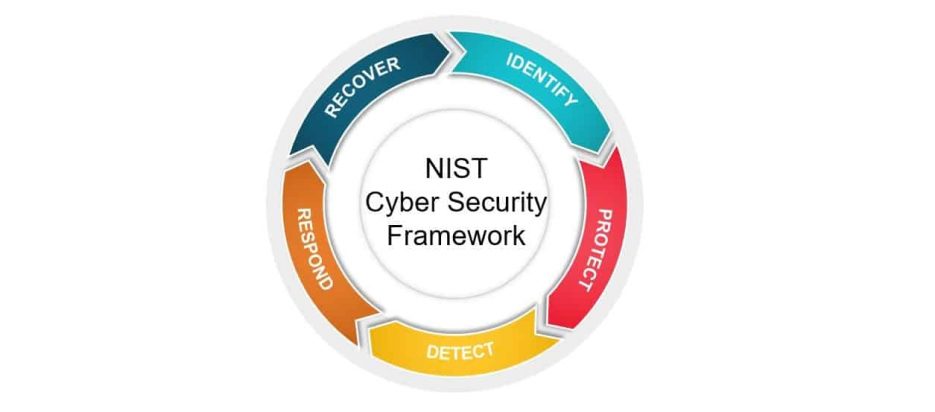
Some organizations use security frameworks that provide time-tested best practices, such as the National Institute of Standards and Technology (NIST) Cyber Security Framework (CSF), which is based on five core functions to achieve cyber resilience: identify, protect, detect, respond, and recover.
Cyber resilience addresses the issue by going beyond prevention alone to consistently ensure the integrity of your critical data and mitigate risk. This type of resilience requires a recovery solution that guarantees access to all your data, without gaps or data loss, in the event of attack so your operation can get back up and running without delays.
Cyber Resilience: Stay Ahead of the Game (part of Ransomware Recovery Guide)
Comparing Resilience - Part 4: Cyber Resilience
Data Recovery and Cyber Resilience
Cybercrimes are designed to bypass preventative measures—and will evolve to keep doing so. Data recovery is the backbone of cyber resilience. Recovering from cyberattacks requires a modern data management and recovery solution that protects across multiple platforms, including on-premises, cloud, tiered storage, and SaaS applications. An effective recovery plan means your organization can avoid downtime, business disruption, and huge financial hits.
An effective recovery plan means your organization can avoid downtime, business disruption, and huge financial hits when malicious actors attempt to compromise your IT environment. As such, IT resilience is clearly a key component of cyber resilience.
Beat Ransomware with Recoverware
Cyber-Resilience: Carpe Data and Fight Back Against Ransomware
Zerto for Cyber Resilience
With Zerto, your business can build a comprehensive cyber resilience plan that will help you face growing cyber threats with confidence. With advanced, world-class continuous data protection and cloud data management, Zerto gives you multiple recovery options to minimize downtime and data loss from cyberattacks, operational loss, or any disaster.
Fully automated failover and failback help you restore corrupt applications and data within minutes, so you never have to pay a ransom or try to reinvent lost work. Zerto combines granular journal technology with long-term repositories, providing a continuous stream of recovery points from any point in time, whether seconds, hours, months, or even years in the past.
Zerto for Ransomware Recovery
Manage and Mitigate the High Cost of Ransomware
Other Resources
Find even more information relevant to what you want to learn and explore through one of the resources below.
LATEST FROM ZERTO SEE ALL
Resource Center
Discover and access content from Zerto and 3rd parties (IDC, Gartner, ESG, etc.) related to cybersecurity and cyber resilience.
Ransomware Recovery Guide
From the definition of ransomware, description of how a ransomware attack unfolds, right down to cyber resilience and ransomware recovery, we cover everything in this ultimate guide.
Man-made Disruption: Ransomware
Ransomware attacks are capable of causing wide-spread disruption over supply-chains, services, institutions and more. Learn how to recover from them.
What is Zerto?
Learn about Zerto and how it can help you solve your data protection and recovery challenges.