Cyber Vault
A-to-Zerto Glossary of Terms
Overview
Cyber vaults represent the pinnacle of secure cyber resilience solutions, designed to safeguard critical data and applications against cyber threats and data loss. They often act as a last line of defense. Cyber vaults play a pivotal role in cyber resilience by aiding containment and cyber recovery efforts. They are part of a comprehensive data protection strategy that includes archive, backup, disaster recovery (DR), and cyber recovery (CR).
Related Topics
What Is a Cyber Vault?
A cyber vault is a key component of a robust cyber recovery and business continuity plan.
Cyber vaults may offer a range of features and can enhance traditional backup and DR solutions by providing not only replication but added cyber recovery measures. Cyber vaults can be purpose-built, integrated solutions, addressing the specific problem of malicious intent by leveraging special integrated features that ensure data integrity.
True vaults are completely offline, providing a clean room or isolated recovery environment where mission-critical services can be restored quickly and efficiently, even in the face of increasingly complex cyber threats targeting backup snapshots.
By centralizing data within an air gapped, immutable backup, cyber vaults ensure that data remains intact and accessible to the right people.
A cyber vault can also aid in rapid recovery by including the important step of quickly identifying clean recovery points with precision. Orchestration and automation can further ensure rapid recovery and minimized data loss.
Why You Need a Cyber Vault to Improve Cyber Resilience
Cyber vaults offer several key benefits that are essential for improving cyber resilience in today’s dynamic landscape. First, they provide an ironclad infrastructure for critical data and applications, offering a safe haven against cyber threats such as ransomware and data breaches.
Moreover, cyber vaults are vital in helping organizations meet compliance and regulatory requirements. With data protection regulations becoming increasingly stringent, such as GDPR, HIPAA, DORA, NIS2, and SOX, businesses must ensure the confidentiality, integrity, and availability of their data. Cyber vaults serve as a key compliance enabler by providing a secure environment for storing and managing sensitive data, facilitating audits, and demonstrating adherence to regulatory mandates.
Comparing Resilience – Part Four: Cyber Resilience
What is Cyber Resilience
The Top 5 Things a True Cyber Vault Should Provide
Most cyber vaults can deliver immutability and detection. Better ones will add rapid recovery to the mix. But only a true cyber vault will also offer an air gap to keep your data immutable, as well as offering all-flash, high-performance storage to act as a clean room for performing your recovery operations.
The top five things that a cyber vault should provide are:
Minimized data Loss and downtime
A cyber vault minimizes the impact of cyberattacks by enabling rapid recovery through automated orchestration, often reducing recovery times from over a month to hours.
Immutability
Ensures that critical data remains unaltered and tamper-proof, providing data integrity and a safe foundation for recovery.
Clean room (isolated recovery environment)
Offers a pristine environment that is free from the contamination of cyber threats for teams to perform recovery operations.
True air gap
Provides a complete offline recovery option, safeguarding your data from unauthorized access and ensuring that only trusted parties can initiate recovery.
Real-time detection
Integrates real-time encryption detection to identify secure recovery points after an attack is underway. This feature ensures that when it is time to recover, teams are choosing clean, uncorrupted checkpoints. Detection also scans for incoming threats, enhancing your existing security stack through easy interoperability and open APIs.
The Importance of Isolated Recovery Environments and Immutable Cyber Data Vaults
What Is an Air Gap in Data Protection
What Is the Best Type of Cyber Vault Solution?
Cyber vaults can involve a complex architecture of hardware, networking, and compute elements—as well as recovery software whose functionality is contingent on the successful interplay of all of these.
It is often better to use a solution from a single vendor to ensure tight integration among all components. A single-vendor solution can provide:
- Seamless interoperability: An integrated, validated, purpose-built solution can result in a more cohesive and efficient cyber vault. By controlling all aspects of the system, a single vendor can optimize performance and ensure compatibility among components. The objective is to achieve CR by design—a unified solution that is fully tested and supported by engineers specializing in cyber resilience.
- Comprehensive support: An integrated solution typically comes with wraparound technical support, streamlining management and maintenance. With a single point of contact for hardware, software, and networking issues, organizations can reduce troubleshooting time and costs.
- Lower total cost of ownership: This consolidated approach often translates to a lower total cost of ownership (TCO).
Cyber Vault and the NIST Cybersecurity Framework
Cyber vaults serve as essential components in meeting various cybersecurity standards, such as NIST. These secure infrastructures provide robust protection mechanisms by employing encryption, access controls, and other security measures to safeguard critical data and applications.
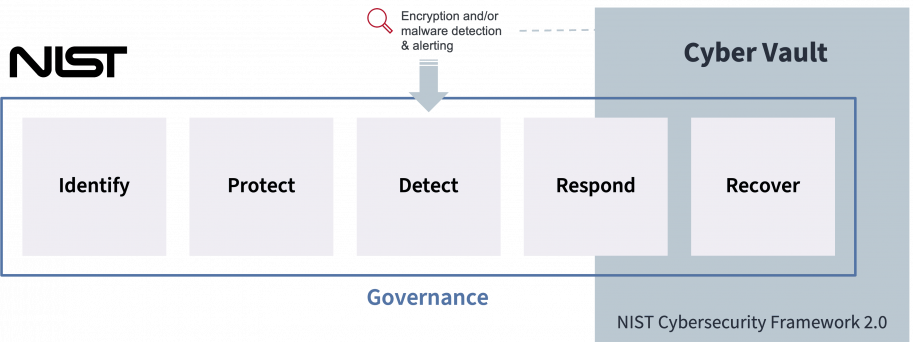
Additionally, modern cyber vault environments should include detection capabilities, enabling early identification of cyber threats. By monitoring for anomalies and suspicious activities, organizations can respond swiftly, limiting the propagation of attacks and minimizing potential damage.
Finally, cyber vaults play a crucial role in recovery efforts by maintaining resilient backup infrastructure and immutable backups. This supports quick restoration of operations, maintaining business continuity, and improving cyber resilience, ultimately enabling a confident recovery.
Why Real-Time Encryption Detection Matters
What Is Real-Time Encryption Detection?
Zerto’s Cyber Resilience Vault: Rapid Air-Gapped Recovery
The Zerto Cyber Resilience Vault by Zerto, a Hewlett Packard Enterprise Company, is a purpose-built isolated recovery environment and immutable data vault combined into a single solution.
It’s expertly designed upon production-grade storage, compute, and networking to help organizations unlock rapid air-gapped recovery from even the worst and widespread cyberattacks.
By using the only dedicated cyber recovery solution on the market to utilize continuous data protection, organizations can see potential reductions in RTOs and RPOs against other cyber recovery vault solutions in the market.
Zerto Cyber Resilience Vault
Why Zerto Cyber Resilience Vault
Other Resources
LATEST FROM ZERTO SEE ALL
Cyber Vaults
Check the available Zerto resources about cyber vaults.
Building a Cyber Resilience Vault with Zerto
Learn about Zerto’s vault architecture, combining Zerto’s ultra-low RPOs and RTOs with the untouchable performance of HPE hardware, and enabling you to architect and customize an ironclad recovery vault.
Essential Guide: Ransomware Recovery
From the definition of ransomware, description of how a ransomware attack unfolds, right down to cyber resilience and ransomware recovery, we cover everything in this ultimate guide.
What is Zerto?
Learn about Zerto and how it can help you solve your data protection and recovery challenges.