Ransomware Recovery
The Only Guide You Will Need
From the definition of ransomware, description of how a ransomware attack unfolds, right down to cyber resilience and ransomware recovery, we cover everything in this ultimate Ransomware Recovery guide.
20 min Read
What do we mean by ‘Ransomware Recovery’?
The ability to recover from a ransomware attack is as important to your business as building the best protection against it. This is even more so with the number of ransomware attacks on the rise.

Ransomware is a type of malicious software that encrypts your files and folders and then demands a ransom to decrypt them. If you don’t pay, the data is deleted, or worse, exfiltrated to the dark web and sold.
Ransomware attacks aren’t isolated to any industry but education, healthcare, and financial institutions are often favorite targets. Any business that uses the internet is a target and susceptible to a ransomware attack.
These attacks are successful because most businesses do not have a proper recovery plan that has been fully fleshed out and practiced. Without a DR plan in place, companies are at the mercy of the criminals. After the attack, they find themselves having to pay the ransom to unlock the system or application, or they’re paying to prevent the exposure of exfiltrated customer data.
Ransomware Attacks
Ransomware attacks are a form of advanced persistent threat (ATP) in which hackers or hacking groups run an attack campaign to penetrate an organization's network and establish a long-term presence in order to access as much data as possible.
Ransomware can enter your network in a variety of ways, most often though it comes in through an email in the form of a phishing email. When someone clicks on the phishing email, it will often download a piece of software that acts as a back door. This software communicates out to a command and control server that will then send more software, including the ransomware payload. Once the ransomware is in the host system it will execute and begin encrypting files and folders, as well as expanding out to the network.
Ransomware attacks are not immediate. Once the initial software connects to the command and control server, the hackers use tools to perform enumeration or network reconnaissance. This ensures that they can encrypt the most important files, and sometimes the backups as well, in order to cause the most damage and force the business to pay the ransom.
7 Stages of a Ransomware Attack
Experience has taught security analysts that ransomware attacks have seven specific, identifiable stages: the 7 stages of the storm.

The Calm Before the Storm
These are the first three stages of a ransomware attack.
These 3 stages identify how the ransomware may get inside your system, which is usually unnoticeable although you may notice performance issues.
Stage 1 - Initiation: this where the attackers infiltrate your system.
Stage 2 - Instantiation: this occurs once the ransomware has infiltrated your system.
Stage 3 - Activation: at this stage, the attackers activate, or execute, the ransomware attack remotely.

The 7 Stages of a Ransomware Attack
Five Types of Cyberattacks You Need to Know
Managing Cyberthreats to Combat Ransomware (3-part mini-series)
The Storm
Once you get to these four stages, your systems will be encrypted, and a ransom note will be delivered.
You can either pay the ransom, usually using a cryptocurrency such as bitcoin, and wait for the hacker to unlock your systems or have a recovery plan that safeguards your business. After that, systems need to be brought online slowly and examined to make sure there is no residual code that will trigger the ransomware again.
Stage 4 - Encryption: Ransomware holds data hostage through encryption.
Stage 5 - Random Request: You’re presented with information on how to pay a ransom via a cryptocurrency transaction.
Stage 6 - Recovery or Ransom: This is the stage where many of the organizations we’ve seen in the news experienced impacts of significant downtime or disruption.
Stage 7 - Clean Up: Once the malware has been cleaned up, the system can be returned to normal operation.
Evolution of Ransomware Attacks
Two new and disturbing trends in ransomware are third-party attack vectors and double extortion.
Ransomware through 3rd party attack vector. This happens when hackers target a third party to try and gain access to an organization's network. From there, they can launch a ransomware attack or simply spy and exfiltrate data. The Solar Winds breach is an example of this — called a supply chain attack¹— where advanced hackers hid their malware code inside of the regular software and then executed the payloads once the customer updated their software. In this case the hack was used to spy on organizations.
Double extortion attacks. As mentioned in Cybercrime Magazine², in this second evolution, hackers move from a basic lock-your-system-until-you-pay ransomware scheme, to a multi-pronged attacks that adds data exfiltration. This allows the hackers to add an additional threat: making data publicly available if they are not paid.
The Cost of Ransomware
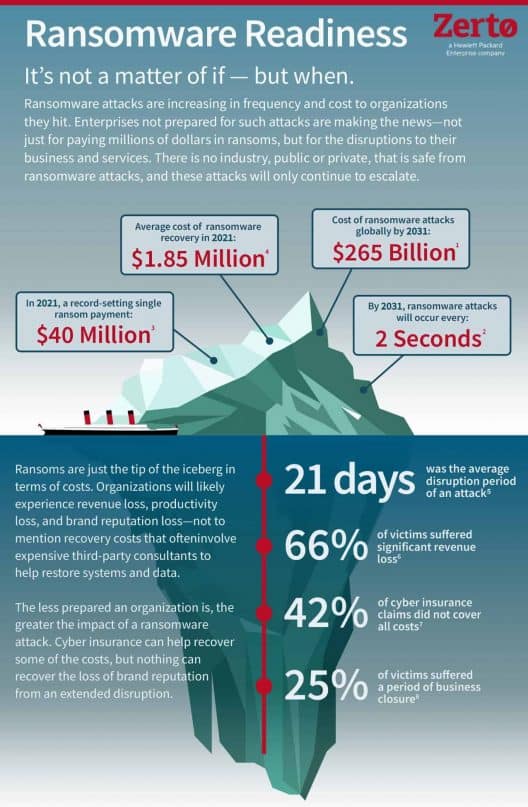
Discovering the initial attack is only the tip of the iceberg. Downtime can last days and take months to fully recover and move on.
And there is zero guarantee you will get your data back, even if you decide to pay the ransom. You’ve read the statistics and seen the costly results. Ransomware attacks are rising year over year.
Sophos reports that 59% of organizations were hit by ransomware attacks between 2023 and 2024, with 70% of the incidents leading to data encryption(1). Highlighting the scale of the threat, Microsoft disclosed that its customers faced over 600 million attacks daily, with remote encryption occurring in 70% of successful attacks(2). In addition to the increased number of incidents, the average cost of recovery grew significantly. In 2024 the average cost was $2.73 million—nearly $1 million more than in 2023(3).
The targets of attacks have also evolved, with 94% of victims saying attackers targeted their backups. Of those attacks, 57% of backup compromise attempts were successful(4).
Looking ahead, experts predict that by 2031, ransomware will attack an organization, consumer, or device every two seconds(5). Meanwhile, AI-powered cyber threats appear to be on the rise, with 74% of survey respondents seeing these threats significantly impact their organizations(6).
Cybercriminals continue to profit from ransomware attacks, leaving no business immune. However, not all business respond in the same way.
- https://www.sophos.com/en-us/content/state-of-ransomware
- https://www.microsoft.com/en-us/security/security-insider/intelligence-reports/microsoft-digital-defense-report-2024
- https://www.sophos.com/en-us/press/press-releases/2024/04/ransomware-payments-increase-500-last-year-finds-sophos-state
- https://www.zerto.com/page/idc-the-state-of-disaster-recovery-and-cyber-recovery-2024-2025
- https://cybersecurityventures.com/ransomware-report-2021/
- https://darktrace.com/resources/state-of-ai-cyber-security-2024
The Colonial Pipeline Ransomware Attack
Tencate Recovers from Ransomware: Before and After
The Colonial Pipeline Ransomware Attack.
In May 2021, the Colonial Pipeline, a 5,500 mile pipeline that supplies upwards of 45% of the gasoline delivered to the east coast of the United States, was brought to an unprecedented halt due to a ransomware attack. This event, which made national headlines, triggered gasoline panic buying that caused sharp shortages at gas stations in many states.
Bloomberg⁵ reported that a USD $4.4 million ransom was paid to the hacker group "Darkside".
The report states that the decryption key received from the group was slow to work, and that the company had been attempting to restore from backups taken prior to the incident.
Travelex systems offline for weeks.
On New Year's Eve 2020, Travelex operations were crippled by a ransomware attack. As a result the company took down its websites across 30 countries. Travelex's partners were also affected by the disruption as they could no longer fulfill their foreign currency purchasing services.
As reported by the Wall Street Journal⁶, Travelex paid the equivalent of USD $2.3 million to the hackers. "The company reinstated some of its operations in January, and revived its consumer business in the second half of February.", i.e. it took more than one and half months to recover.
Tencate: 2 ransomware attacks, 2 different outcomes.
Tencate, a multinational textiles company based in the Netherlands, experienced ransomware attacks twice.
The first time, one of its manufacturing facilities was hit with CryptoLocker, which infected all its file servers. At that time Tencate was only able to restore from disk and as result experienced 12 hours of data loss, was not able to recover for two weeks.
The second time, a more advanced form of CryptoLocker hit a manufacturing faciity, but this time Tencate had a distaster recovery solution based on continuous data protection (CDP). The result: 10 seconds of data loss and full recovery under 10 minutes.
Cyber Resilience: How to Stay Ahead of the Game
There is an old saying, the best time to prepare for a storm is before the storm hits, the next best time is now.
Every cyber security plan should be about preventing ransomware attacks before they happen. However, cyber-attacks and cyber-crimes by their nature are designed to bypass preventative measures and continue to evolve rapidly in order to do so. Organizations that take these threats seriously know that it is a matter of when, not if, they will be attacked.
When that happens, only an effective recovery plan will allow your organization to avoid downtime, business disruption and taking a huge financial hit. The key to ransomware survival, like any disaster, is to prepare ahead of time and plan for specific scenarios. Once you have a plan in place, you need to practice until it becomes second nature, so all the members of the incident response team know their roles, responses, and responsibilities.
Planning ahead and accounting for the inevitable ransomware attacks is known as cyber resilience within cyber security groups, or IT resilience within IT teams.
Comparing Resilience: Business, Operational, IT and Cyber (5-part Mini-series)
Cyber-Resilience: Carpe Data and Fight Back Against Ransomware
A Resilient Approach to Ransomware
An IT resilience framework usually has two parts, an infrastructure side, and a security side.
Infrastructure: this side considers data availability. To ensure maximum availability, you usually have your data replicated across geographically distributed data centers,
so that if there is a physical disaster that impacts one site, data operations can continue uninterrupted. To access this distributed data, you need as fast of a high-speed connection as possible. Alternatively, to the data center distribution, you can implement a cloud first strategy, which places the
infrastructure burden on the cloud provider.
Security: this involves more specifically how data is protected, backed up, and recovered. A standard disaster recovery and business continuity plan would provide the basic framework of the proper security controls to ensure data integrity and accessibility. But to truly ensure the highest available recovery time, you will need to implement some form of continuous data protection (CDP). This ensures that any changes to protected systems are recorded and can be recovered to and within seconds.
Business resilience, or business continuity, has many components but within IT, the ability to recover data is the backbone of resilience. Backup and disaster recovery operations can be effective, whether restoring files locally or recovering applications from a secondary DR site to help your organization get back on track. Modern ransomware attacks require modern data management and recovery solutions that protect data across multiple platforms including on-premises, cloud, tiered storage, and SaaS applications.
Ransomware Readiness
If you haven’t started planning for recovery, now is the time. If you have planned, now may be the time to review your plans.
Effective preparation to ensure you can recover is the most critical line of defense against the disruption and attacks that make the news. While you won’t be able to stop all attacks, creating a comprehensive cybersecurity and disaster recovery plan is paramount to minimizing your risk.
That was the intention behind the Cybersecurity Framework⁷ launched by the U.S. Commerce department’s National Institute of Standards and Technology (NIST). This flexible framework helps organizations understand the best practices they should use to manage their cybersecurity-related risk, centered on these core functions⁸:
- Identify | 2. Protect | 3. Detect | 4. Respond | 5. Recover
NIST identifies these functions as “the five primary pillars for a successful and holistic cybersecurity program. Your Ransomware readiness checklist should cover them all.
Ransomware: How to Protect Yourself Before It is Too Late
Ransomware Readiness Checklist
How to Recover from Ransomware
Ransomware Prevention
This is where most of the cyber security defenses that covers the first three pillars of the NIST framework —Identify, Protect and Detect— are enacted. Defenses include: antivirus solution, network protection, real-time encryption detection, identity management, vulnerability management and patching, and security operations to detect attacks. Security trainings for employees and IT staff, along with Pen testing, ultimately help to make defenses stronger.
Disaster Recovery Solution
While ransomware prevention is all about preventing and defeating the attacks, the disaster recovery (DR) solution goal is to ensure there is data and/or the infrastructure available to restore operations as quickly as possible, with the minimal amount of data loss and the shortest downtime. The choice of the DR solution will be essential in delivering recovery times —RTOs and RPOs— deemed acceptable by the organization, and in allowing frequent testing to ensure readiness when ransomware strikes.
Ransomware Response and Recovery Plan
Defenses have been breached. It is now time to respond. Effective communication between all the actors part of the response team is essential. Frequent training, well documented and executed processes, flows and protocols, are what makes the difference in such chaotic and time sensitive situations.
The speed and reliability of the response can be further enhanced with a DR solution that can be leveraged for cyber forensics — environment cloning— and that allows for testing the recovery in isolation prior to recovering to production.
While many organizations do a good job with the first four pillars of the NIST Cybersecurity Framework⁷, they struggle or leave gaps over recovery. An IDC survey (2022 Ransomware Strategy Survey), sponsored by Zerto, revealed that two thirds of respondents thought that their recovery strategies needed further examination. Having an effective disaster recovery plan alongside an adequate DR solutions is key to overcome this challenge. This is where what we call Recoverware comes into play.
What NOT to Do When Planning Ahead of Ransomware
There are few things you should be aware of and try to learn from others' mistakes.
This is by no means an exhaustive list of things to consider but it highlights some of the very important points.
Recoverware: Useful or Not in Ransomware Recovery?
Recoverware is much more than software. It is an effective disaster recovery solution coupled with a business process and plan to carry out recovery.
In the battle of ransomware, having a recovery-first mentality is a significant deviation from regular business practices. In regular processes, businesses invest in recovery solutions and approach the threat of ransomware from a what if mentality, as in “what if” we get attacked. But the reality shows that the likelihood of an attack is no longer a matter of "if", but "when".
Recoverware takes on ransomware directly by providing the recovery options necessary to bring systems back online with a very recent replica of the data if detected quickly, or a copy of the data from long-term retention, and do so in a safe, tested environment. While security specialists focus on prevention, Recoverware provides the safety net against the attacks that will inevitably make it into the system.
Recoverware is not merely a marketing term coined to grab attention. It is an honest attempt to define a class of recovery solutions, that can counteract ransomware when prevention has failed.

Beat Ransomware with Recoverware
Continuous Data Protection
Recovery: The Ultimate Line of Defense Against Ransomware
Continuous Data Protection in Recoverware
Continuous data protection (CDP) is a critical component in the idea of recoverware which is the integration of data recovery processes into the overall architecture and strategy of information technology.
CDP is the most effective method of ransomware mitigation. At its heart lies the continuous replication of your data, performed any time there is a change to the data.
CDP allows for a granular recovery point and recovery time objective, or RPO and RTO. Continuous data protection can ensure your data loss is minimal and can be used to pinpoint your recovery. In comparison, daily backups and snapshots will have a larger data point loss because the RTO and RPO need to be greater.
In terms of what types of data are suited for CDP, your network files and folders, databases and application data all can utilize this cost-effective system.
Recoverware changes the script that the ransomware attackers are trying to follow by making the disruption and the cost of the attack negligible. Attackers are counting on legacy security thinking and planning with a focus on prevention while recoverware allows organizations to rethink with a focus on modern recovery options.
Key Features in a Ransomware Recovery Solution
Seek out what really matters.
When assessing your current ransomware recovery solution, or when considering a new one, you should review a few key points and ask yourself and/or any potential vendor these questions:
- How quickly can the solution help you get back and running? Or what is the lowest RTO you can achieve?
- How much data will you be able to recover? Or what is the data loss you are going to experience (RPO)?
- Can your solution let you recover your data to an isolated network so that you can perform data sanitization?
- Does the solution have the ability to support multiple copies of the data to allow for flexible recovery options? This is crucial, as is the assurance of an immutable data copy, or data that cannot be modified or deleted.
- Can you perform non disruptive DR testing in the solution so that you can be certain that you can recover when the time comes?
- Does the solution provide on-demand sandbox creation for system hardening and data forensics?
- Does the solution protect all my types of workloads (virtualized, cloud, SaaS)?
The responses to these questions, when evaluating vendors’ solutions, should help you determine the ones that will be best suited to help you to build your ransomware resilience.
Where to Find an Effective Ransomware Recovery Solution?
A solution that fits your BCDR strategy, and delivers on data protection and recovery.
After reading this far, you should have an idea that a ransomware attack isn’t a matter of if, it’s a matter of when. The need for a cyber resilience, or IT resilience strategy is your only real defense against the coming storm.
You can choose to try and find solutions to each of the potential attack vectors and try to tie all of it together, but the reality is that you likely don’t have the time or the expertise to secure all of the parts of your business that ransomware will hit.
The only effective response is a disaster recovery solution that can bring the data and the operations it enables back online as quickly as possible and with the least amount of data loss.

Ransomware Recovery with Zerto
Short video (2 min 45 sec) showcasing how easy it is to recover with Zerto.
Why Choose Zerto for Ransomware Resilience
See What's New in Zerto 10 for Ransomware Resilience
Zerto for Ransomware Recovery
Because ransomware is a disaster scenario, Zerto, a Hewlett-Packard Enterprise company, provides data protection that is perfectly suited for minimizing the disruption caused by any ransomware attack and delivering the very best recovery time objective (RTO) and recovery point objective (RPO) possible.
Zerto offers the rapid maturity of a data protection and recovery solution that integrates cyber resilience, continuous data protection, real-time encryption detection, and sandbox architecture that provides network isolation and enable data forensics.
With easy implementation and deployment, the Zerto solution can scale with your organization to ensure continuous data protection for all of your business-critical and lower tier applications.
As you consider taking a different approach to your ransomware resilience strategy, or simply replacing your existing and frailing solution, make sure to check out and evaluate Zerto for your ransomware recovery needs.
Zerto Cyber Resilience Vault
Unlock rapid air-gapped recovery with an isolated data vault using ultra-secure zero trust architecture, real-time encryption detection and data immutability.
FAQ about Ransomware Recovery
Yes, it is possible for an organization to recover from ransomware, and speed is a critical factor to its success. Recovery speed depends on whether the recovery data remains uncompromised by the attack, the availability of immutable and air-gapped copies, attack scope, and other factors. For some, restoring from backups is feasible, while others might initially consider paying the ransom in hopes of restoring their data more quickly.
Instead, organizations should prioritize fast recovery by leveraging disaster recovery solutions built for cyber recovery. By utilizing a combination of real-time replication, journal-based recovery, failover, immutability, and cyber vaulting, recovery can be performed more rapidly and with much less data loss.
Your organization’s BIA will help determine how much data loss and downtime your organization can tolerate and set your RPOs and RTOs. Use this analysis to guide decisions on what tools you will use for data protection and recovery—whether that means relying on backups that might be infrequent and slow to recover, or disaster recovery solutions including immutability and isolation with minimal data loss and rapid recovery.
Although the average downtime for organizations following a ransomware attack varies depending on the industry and specific circumstances of the attack, recovery time can generally range from several days to weeks.
For instance, in healthcare, the average downtime due to ransomware attacks was approximately 18.71 days¹. In broader contexts, some data indicates that ransomware recovery takes about 21 days².
Sources:
- https://www.statista.com/statistics/1422159/us-healthcare-ransomware-attacks-downtime-average-by-days
- https://www.cigent.com/blog/ransomware-and-recovery-time-what-you-should-expect
A ransomware recovery plan aims to restore data and systems quickly with minimal downtime and data loss after an attack. These plans can be tailored by workload priority, such as rapid recovery plans for critical workloads using immutable, air-gapped copies, a high-performance clean room environment, orchestration and automation, and traditional recovery methods for noncritical systems.
Ransomware recovery plans are a key element of cyber recovery, which forms the backbone of ransomware and cyber resilience.
MORE RESOURCES ON RANSOMWARE SEE ALL
Ransomware? Recoverware
Zerto's continuous data protection (CDP) delivers recovery for ransomware.
Ransomware Preparation: Cloning for DevTest and Non-disruptive Patching
Learn how Zerto, on top of its recovery capabilities, arms your teams to further enhance your cybersecurity defenses.
What is Zerto?
Learn about Zerto and how it can help you solve your data protection and recovery challenges.
1. Techtarget - Supply chain [cyber] attack
2. IDC - out of 500 organiozations, 84% were victims of malicious attacks in 2019 ... from blog: https://www.zerto.com/blog/ransomware-recovery/cyber-resilience-carpe-data-and-fight-back-against-ransomware/ -> NEED SOURCE
3. Cybercrime Magazine - Global Ransomware Damage Costs Predicted To Exceed $265 Billion By 2031
4. Cybercrime Magazine - Global Ransomware Damage Costs Predicted To Reach $20 Billion (USD) By 2021
5. Bloomberg - Hackers Breached Colonial Pipeline Using Compromised Password
6. WSJ - Travelex Paid Hackers Multimillion Dollar Ransom Before Hitting New Obstacles Story
7. NIST Cybersecurity Framework - Overview
8. NIST Cybersecurity Framework - The Five Functions
9. Container Journal - Protecting Kubernetes from Ransomware Threats