Ransomware Resilience Solution
Preventing ransomware isn’t always possible — but mitigating the damage is. Detect in seconds and recover in minutes, at scale, to a state seconds before an attack. Only Zerto can do that.
Recovery is the Cornerstone of Ransomware Resilience
Understand the fundamentals of ransomware resilience and see how Zerto enables you to protect your business and establish a recovery plan.
Ransomware Attacks Grow in Severity and Scale
Preventing ransomware is no longer enough. Increasingly sophisticated malware can slip through your defenses, encrypt your critical data, and cripple your business. With data now in disparate locations and workloads — and in the hands of more users than ever — rapid detection and recovery is key when an attack gets through. After all, no organization is immune from an attack. A study from IDC found that
- 79% of those surveyed activated a disaster response
- 83% experienced data corruption from an attack
- Nearly 60% experienced uncoverable data
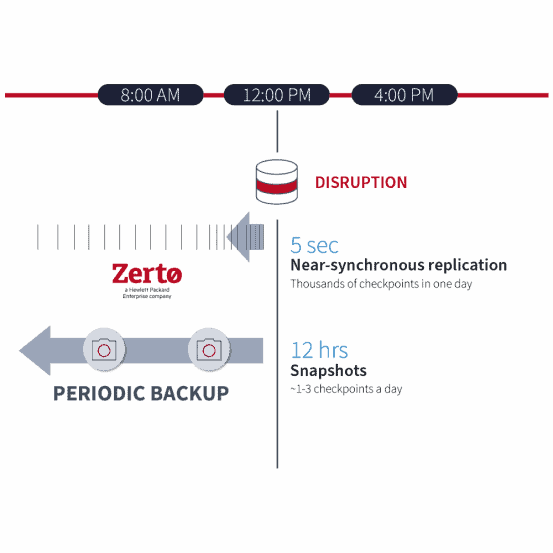
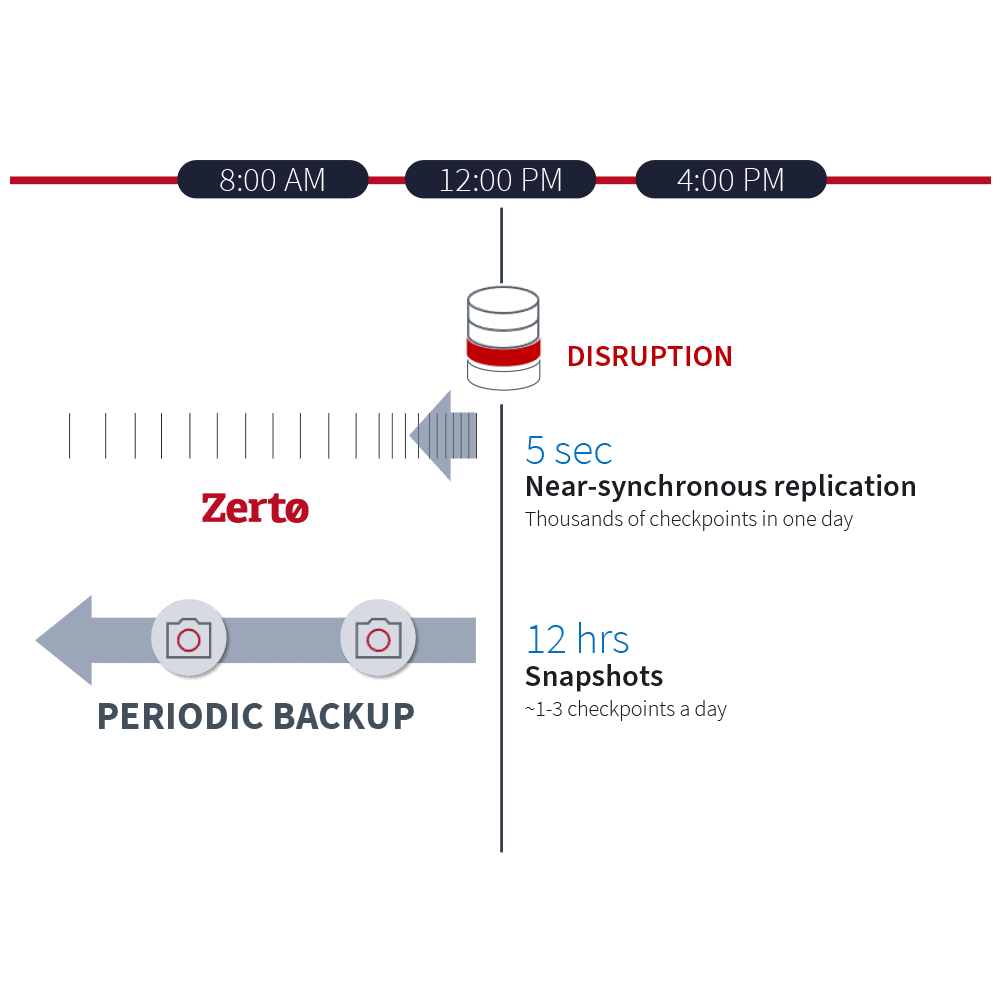
Unlike backup solutions, only Zerto’s continuous data protection (CDP) technology mitigates costly risks like data loss, downtime, and disruptive recovery testing.
Take the Stress Out of Ransomware Recovery
Dramatically mitigate the risks and impact of cyberattacks by having the right ransomware resilience strategy in place.
Detect encryption within seconds and recover corrupted applications and data within minutes of initial infection with Zerto’s automated restores.
Why Zerto for Ransomware Resilience
Cyberattacks Survival Kit

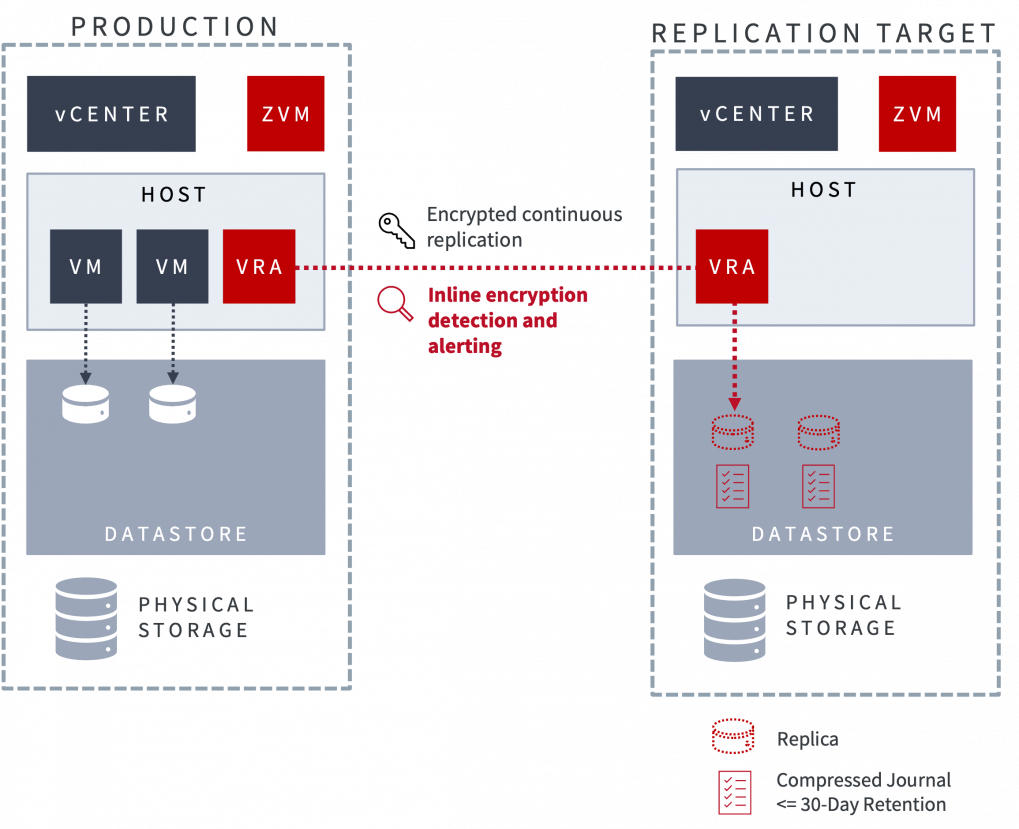
Real-Time Ransomware Detection in Seconds
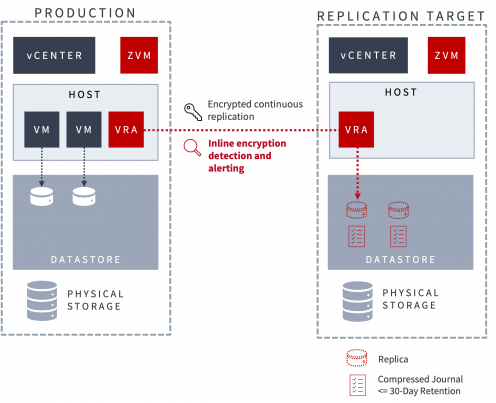
Using Zerto’s continuous data protection engine, with its always-on replication and journaling technology, data encryption from a ransomware attack can be detected within seconds. Real-time alerts can send incident response teams into action to isolate and mitigate the attack and begin the recovery process.
Don't wait for the next backup to detect ransomware
Real-time detection not only alerts you faster than competing solutions but tags checkpoints in the recovery journal to help you pinpoint when the attack began and recover data in a good state to a point seconds before encryption.
Reduce the cost and impact of a ransomware attack by detecting it more quickly and recovering more quickly with real-time detection.
Zerto Real-Time Ransomware Detection
Gorilla Guide to Real-Time Ransomware Detection and Recovery
Ransomware Resilience and Recovery in Minutes, At Scale
Leverage Zerto’s continuous data protection, with its always-on replication and journaling technology, to recover entire sites and applications at scale, with only seconds of data loss — and resume operations.
Recover to a State Seconds Before an Attack
With just a few clicks, recover your multi-VM applications to a point in time just seconds prior to an attack. Applications and all their VMs are recovered as one single, crash-consistent unit.
Using built-in orchestration and automation, you can easily failover an entire site — without disruption.
How to Recover from Ransomware
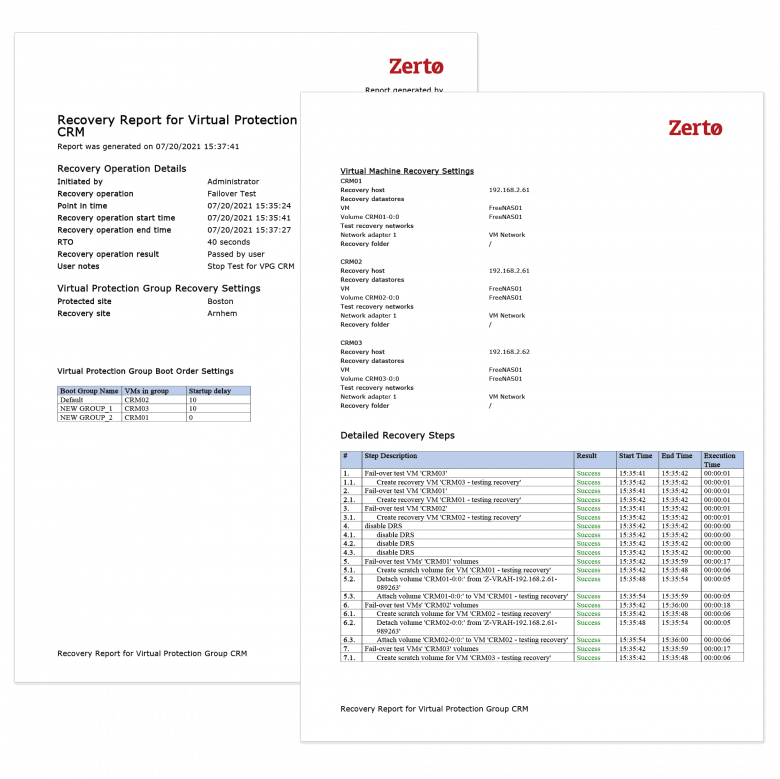
Lower Risk with Instant, Non-disruptive Testing
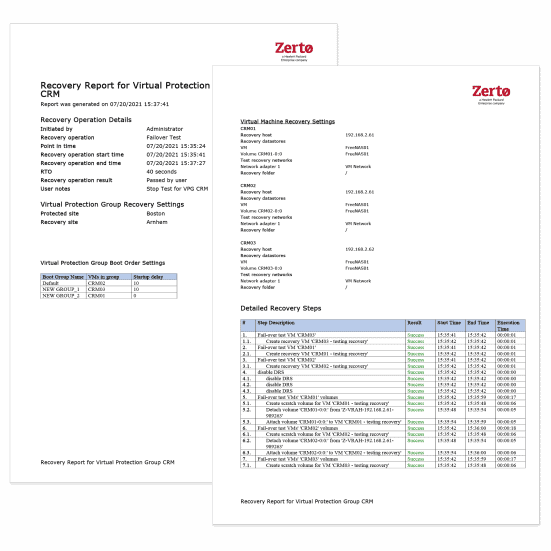
Malware hackers use more sophisticated tactics each day, so testing your data protection solution regularly is crucial. Gain confidence by frequently testing both failover and recovery quickly – at any time, with full compliance reporting, and without disruption to your production environment.
Explore Zerto’s Automated Disaster Recovery Testing Abilities
Achieve Maximum Ransomware Reslience with the Cyber Resilience Vault
Achieve the ultimate last line of ransomware resilience with the Zerto Cyber Resilience Vault. The offline, locked-down vault combines Zerto’s award-winning recovery software with the power of HPE Alletra storage, HPE ProLiant servers, and HPE Aruba networking. The Cyber Resilience Vault uses isolated, air-gapped, zero trust architecture with immutable data copies to ensure rapid recovery when all else fails.
Zerto Cyber Resilience Vault
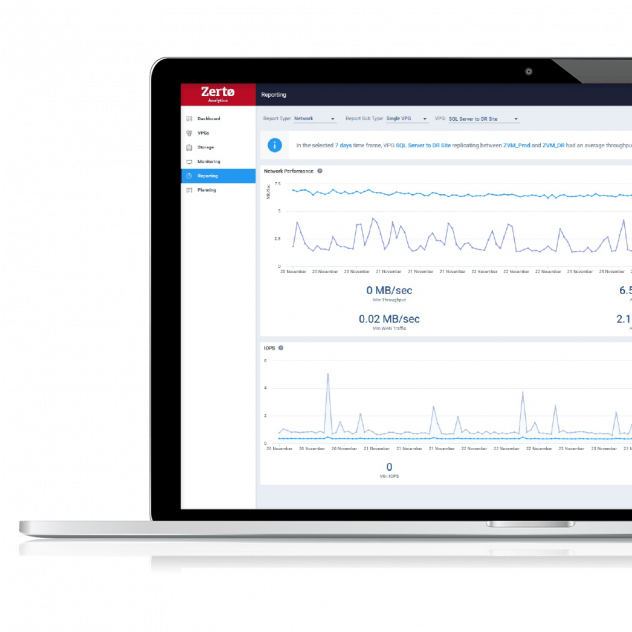
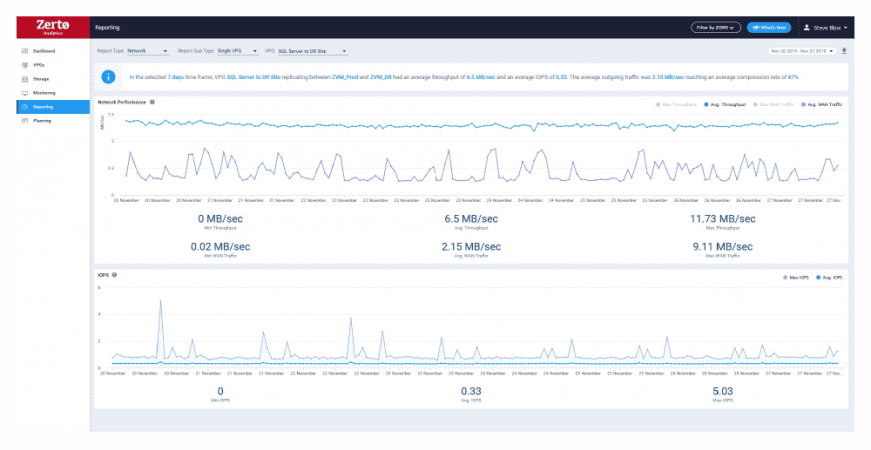
Intelligent Insights with Zerto Analytics
Built-in intelligent dashboards and reports help you to spot trends, analyze unusual traffic, and forecast infrastructure requirements to support your ransomware resilience initiatives.
Explore Zerto Analytics
Recover Confidently with Immutable Data Copies
Immutable data copies are untouchable by ransomware so hackers can’t encrypt or deleted your data in an attack. Recover your data confidently after an attack with Zerto’s built-in immutability with:
- Immutable data copies that can be stored within Microsoft Azure Blob Storage
- Microsoft Azure and AWS S3-compatible storage as a destination for immutable data copies
- Zerto Backup for SaaS for offsite immutable backups of Azure Active Directory, a critical component for recovering quickly from ransomware
Explore Solutions with Immutable Storage
Immutable Cyber Recovery Services Built on Zerto and Hosted by Your MSP

Ransomware Recovery Scenarios with Zerto
In this mini-series, see how Zerto’s flexibility unlocks multi-cloud recovery of files, VMs, or entire applications no matter how severe the ransomware attack.
Ransomware Recovery After File Encryption
The first in a series on ransomware recovery with Zerto, this video looks at a small-scale attack that has encrypted files and folders on a VM and discusses how Zerto can get you out of ransomware jail using instant file restores.
(2 min 29 sec)
Ransomware After VM Encryption
The second in a series on ransomware recovery with Zerto, this video looks at an attack that has compromised an entire VM and discusses how Zerto can get you out of ransomware jail using instant VM restores.
(1 min 50 sec)
Ransomware Recovery After Application Infection
The third in a series on ransomware recovery with Zerto, this video looks at an attack that has infected all VMs that comprise a multi-VM app stack and how Zerto can get you out of ransomware jail using orchestrated failovers to a peer site.
(2 min 49 sec)
Ransomware Recovery After Site Infection
The fourth in a series on ransomware recovery with Zerto, this video looks at an attack that has compromised the infrastructure at all on-premises sites and how Zerto can get you out of ransomware jail using orchestrated failovers to a cloud DR site.
(2 min 35 sec)
Ransomware Recovery After Multi-Site Infection
The fifth and final in a series on ransomware recovery with Zerto, this video looks at an attack that has fully infected all on-premises and cloud infrastructure and how Zerto can get you out of ransomware jail using portable immutable copies that can be re-attached to any new or existing Zerto deployment.
(2 min 53 sec)
Key Benefits of Zerto for Ransomware Resilience
FAQ about Ransomware Resilience
Ransomware resilience is part of a comprehensive cyber resilience strategy that goes beyond prevention alone by strategically addressing the distinct challenges to recovery posed by cyber threats. The backbone of ransomware resilience is cyber recovery, as it enables the fast restoration of systems. Cyber recovery measures should be implemented alongside proactive prevention, incident response, and regulatory compliance.
Effective ransomware resilience includes these critical strategies:
- Preventive measures help to minimize ransomware-induced downtime by implementing safeguards like intrusion detection, immutability, and air gapping, data encryption in case of theft, network segmentation, robust security protocols, regular software updates, readiness testing, and employee training.
- Incident response prioritizes real-time detection to quickly identify clean recovery points, rapid alerting of response teams, and limiting the blast radius to contain damage effectively.
- Cyber recovery mechanisms aim to minimize downtime and data loss by achieving low recovery time objectives (RTOs) and recovery point objectives (RPOs). These mechanisms might include ransomware or cyber recovery plans tailored by workload priority, such as rapid recovery plans for critical workloads using immutable, air-gapped copies, a high-performance clean room environment, and orchestration and automation, and traditional recovery methods for noncritical systems.
- Regulatory compliance enables organizational accountability by adhering to data protection and incident reporting frameworks like GDPR, HIPAA, or SEC regulations.
To build reslience against ransomware, organizations should first assess their estimated recovery times, as well as their tolerance for data loss and downtime. This assessment, often conducted through a business impact analysis (BIA), helps teams choose the most effective recovery methods.
For instance, organizations without rapid cyber recovery solutions might choose to pay a ransom, even if backups are intact, because rebuilding from backups would take longer than acceptable. Conversely, those with rapid cyber recovery solutions can restore systems within acceptable time frames, even if backups are compromised. Use the insights from your analysis to develop a cyber resilience plan tailored to your recovery SLAs and available tools.
What's Next?
Have a question about our product or capabilities? Contact us, we are here to help!
Take a Tour
Take a tour of our solution to learn about Zerto’s features and benefits for yourself.
Try Zerto
Want to give Zerto a try? Get a free 14-day license or access to our on-demand labs.
RECOMMENDED CONTENT SEE ALL
IDC-The State of Disaster Recovery and Cyber Recovery, 2024–2025s
In this IDC white paper, sponsored by Zerto, find information to evaluate your organization’s standing, and assess the state of modern data protection, disaster recovery, cyber recovery, and AI.
ESG 2023 Ransomware Preparedness: Lighting the Way to Readiness and Mitigation
Enterprise Strategy Group conducted a survey of over 600 organizations to gain further insights into what proactive and reactive measures organizations have in place to defend against ransomware. Learn more!
Cyber Resilience Assessment
Zerto's new Cyber Resilience Assessment will help you assess your organization's ability to mitigate the risk of damage to your data and operations and to bounce back unscathed once attacked.