Security and Compliance
Zerto delivers a simple and reportable way to protect, test, and recover your applications
Remain Resilient and Compliant at All Times
From tackling threat vulnerabilities and ensuring cyber resilience to demonstrating compliance, Zerto has your back.
Tackle threat vulnerabilities, ensuring cyber resilience, and demonstrating compliance with Zerto.
Recover from Ransomware
Pass audits and stay compliant with built-in reporting and hassle-free testing.
Automated Compliance Reporting
Execute non-disruptive patch testing against seconds-old true copies of production in an isolated sandbox, all in four clicks.
Non-disruptive Patch Testing
Ransomware Resilience
No more unplanned downtime. Eliminate ransomware data loss and downtime with real-time ransomware detection and continuous data protection.
In addition to staying protected, organizations must ensure they’re able to recover from ransomware. Today's digital landscape requires organizations to accept the reality of ransomware attacks, and take measures to keep their data resilient.
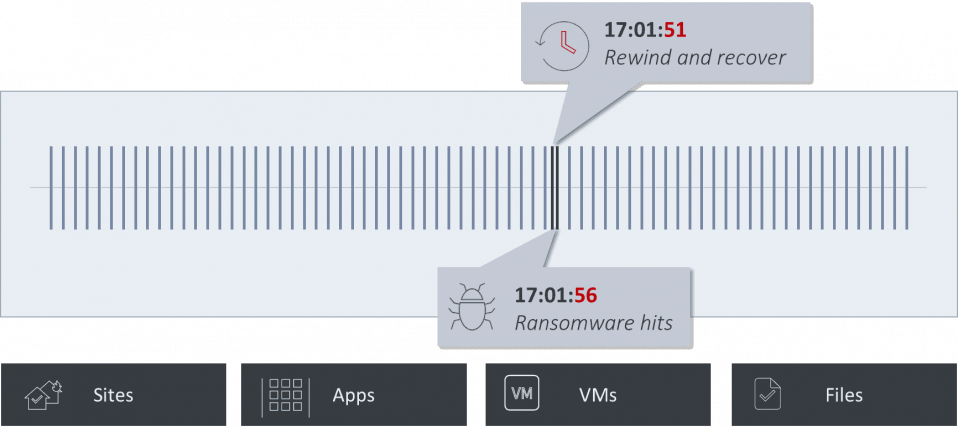
A resilient approach requires you to shift the way you think about ransomware, from an exclusive focus on preventing attacks to advanced preparation for any possibility of attack. Your recovery solution should guarantee access to your data during a disruption, without gaps or data loss, so your operation is back up and running without delays. Because snapshot-based recovery introduces high RPOs and lengthy RTOs, organizations need continuous data protection (CDP) for real-time recovery from ransomware.
Automated Compliance Reporting
Zerto unlocks orchestrated and automated disaster recovery testing, carried out any time, with just four simple clicks. Test without disruptions, as often as your organization requires, while drastically reducing the days and hours spent on disaster recovery testing.
Zerto enables you to:
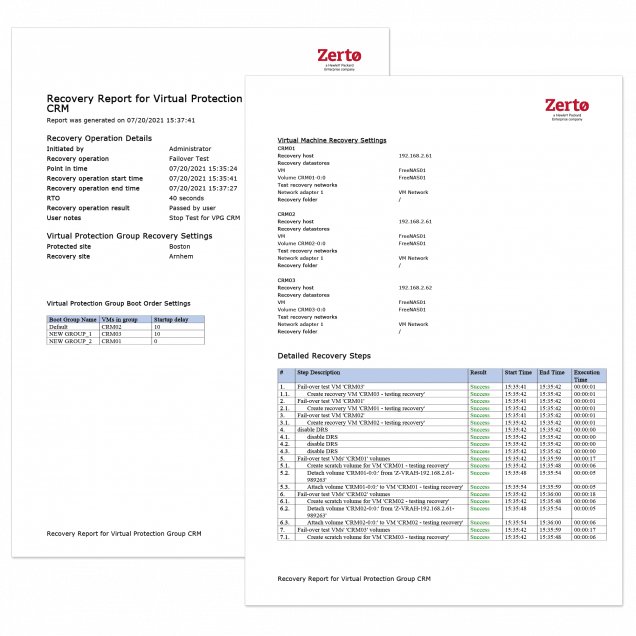
Patch Testing
Patch testing can be disruptive and make any IT pro nervous. Zerto delivers easy, non-disruptive patch testing against seconds-old true copies of production in an isolated sandbox. All in four clicks.
With Zerto's unmatched granularity of seconds, your test clones are only seconds behind their production counterparts, providing a true picture of how a specific patch or upgrade will behave. Startup is automated and orchestrated so you can remain compliant and limit the potential risks of patch testing while reducing the resources and time used.
Recommended Content

Rapid Air-Gapped Recovery with Zerto Cyber Resilience Vault
Achieve the ultimate last line of ransomware resilience with this offline, locked down vault that uses isolated, air-gapped, zero- trust architecture with immutable data copies to ensure rapid recovery when all else fails.

Zerto Real-Time Ransomware Detection
Zerto has innovated new technology to bring real-time encryption detection to the market. You will no longer need to wait hours or days to know when recovery is necessary, radically reducing data loss and downtime following an attack—and doing so without paying any ransoms.

Blog: Ransomware Series
Stay up to date with what's going on around cyber-resilience and ransomware.


